Column-level security (CLS) allows organizations to control access to specific Table columns.
In Snowflake, Column-level security is implemented using Masking Policies.
A Masking Policy in Snowflake is a schema-level object that dynamically masks the data returned in a column of a Snowflake object (such as a table or view) at query time. The masking behavior is determined by conditional expressions and context functions, such as CURRENT_ROLE(), SESSION_USER(), or other supported Snowflake identity functions.
Dynamic Data Masking
Snowflake supports two types of Masking Policies:
-
Tag-Based Masking Policy (Recommended)
-
A Tag-based Masking Policy uses Snowflake Tags to define reusable, scalable masking rules.
A Masking policy is assigned to a tag, and any column carrying that tag automatically applies the associated masking logic across all tables and schemas.
Tag-based masking policies support scalable, classification-driven governance, simplify lifecycle management, and enable consistent enforcement for compliance with regulatory requirements. -
Use Case Example
- A company tags columns such as Customer_Email, Customer_Name, and other sensitive fields across multiple schemas using
PII = 'High'.
It then applies a tag-based masking policy with contextual rules so:- Standard analysts receive masked values
- Support agents receive partially visible values
- A small privileged group has full visibility
- A company tags columns such as Customer_Email, Customer_Name, and other sensitive fields across multiple schemas using
-
- Column-Based Masking Policy
-
A Column-based Masking Policy is attached directly to a specific column in a table or view.
The Masking Policy defines how specific column values should be transformed or hidden for certain users or under certain conditions.
Column-based masking policies support highly specific business logic per column or table and provide tight localized control without changing global behavior. -
Use Case Example
Onlycredit_card_numberin thepaymentstable has the rule:- Support role sees the last 4 digits
- Fraud role sees the full value
- All other users see
*****
-
Creating a Snowflake Masking Policy
Ensure that your Snowflake Application in Orchestration is switched to Manage mode to start building your Masking Policy in the Policy catalog section. See Managing POPs for more information on how to change the POP Mode.
Masking Policies in PlainID can be created using the following methods:
- Wizard
- Code
- Native
For more information, refer to Creating Policies.
To create a Masking Policy with the Policy Wizard:
-
Input the Policy Details. For more information, refer to the Creating Policies article
-
Select Use Policy For SaaS Applications and select the Snowflake application.
-
Input the Snowflake POP Details specific to the vendor Policy:
- Under the Vendor Policy Kind dropdown, select Masking Policy. (Required)
- Enter a Vendor Policy Name, a unique name for the Policy that will appear in the Snowflake vendor. (Required)
- Note: The same name can be used across multiple PlainID Policies to define multiple logic statements within a single Snowflake Masking Policy.
- Under the Vendor Policy ID, note that the ID is automatically generated. It is the ID used in Policy management operations like deploy, update, and override.
- Define the Vendor Policy Order, which relates to the execution order for the logical case statement within the same Vendor Policy ID. (Required).
- The Default value is 1. Use this field when enforcing multiple logic conditions for different Identity Groups within the same Policy.
- Enter a Comment, add any additional information or clarifications about your Policy. (Optional)
- Under Database, select the Snowflake database where the Policy will be deployed.
- Under Schema, select the schema within the database where the Policy resides.
- Input an Owner, provide the POP Snowflake role used to manage the Policy.
-
Click Continue.
Who Section
In the Who section, you can assign Column-level access by creating a new Dynamic Group or selecting an existing one. A single Policy can evaluate multiple Dynamic Groups (OR relationship between them), giving you flexibility in defining access control logic. Select Dynamic Groups associated with Identity Attributes defined in your POP.
Dynamic Groups are defined using Snowflake identity functions such as CURRENT_USER(), CURRENT_ROLE(), IS_ROLE_IN_SESSION(), and CURRENT_SECONDARY_ROLES(). You can use multiple Identity functions within the same group to refine access. If you want to apply your Policy logic to all users, you can still connect the default "All Users" Dynamic Group.
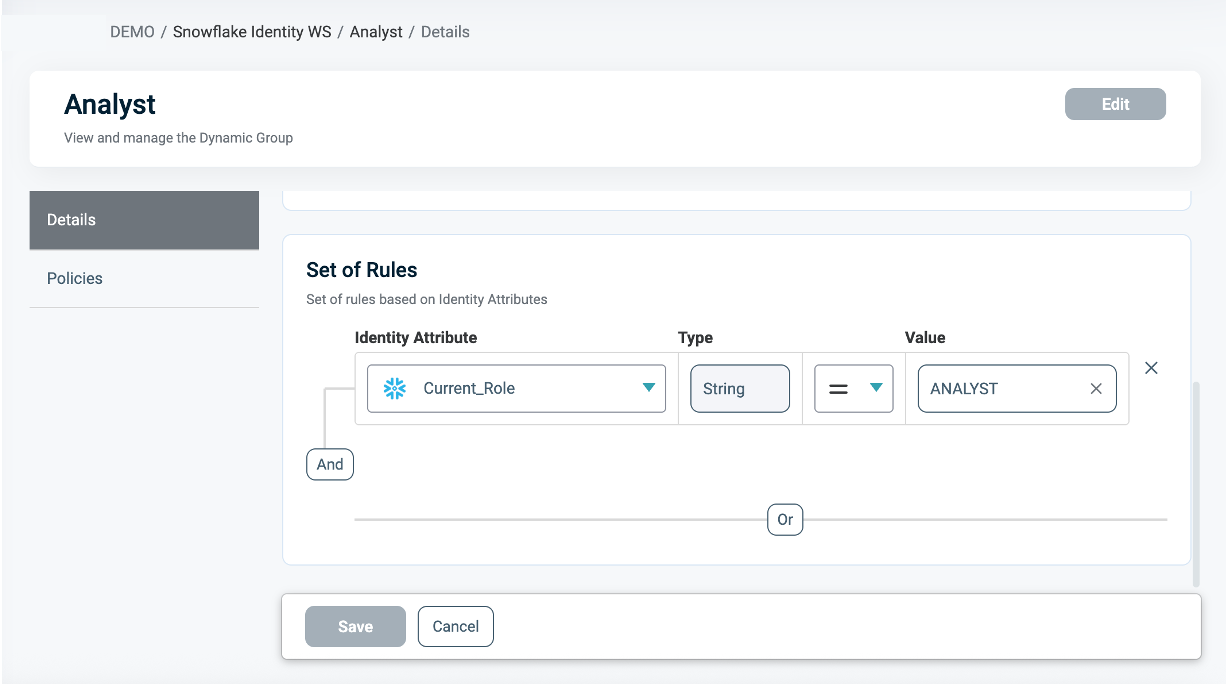
For additional information on how to create a Dynamic group, see Managing Dynamic Groups.
What Section
In the What section, you can define access through your Asset Types.
For more details on Asset Types, refer to Managing Asset Types.
To define access, you are required to define the following Asset Types:
- Click Add Asset Type (for Policy Signature). Ensure that your Asset Type meets the Signature Asset Types for Column Level Requirements listed below
- From the dropdown, select an Asset Type that defines your Masking Policy logic (Policy Signature. See Policy Syntax Table for more information.)
- Only one Asset Type can be selected in a single Masking Policy.
- Select existing Rulesets for your policy logic or create a new one. A Policy can include multiple Rulesets (OR relationship between them).
- See Defining a Ruleset for Masking Policy for more information.
- Click Save.
- From the dropdown, select an Asset Type that defines your Masking Policy logic (Policy Signature. See Policy Syntax Table for more information.)
- To add Snowflake Columns Or Tag Asset Types, click Add Asset Type.
- From the dropdown, select Snowflake Columns Asset Type or Tags Asset Type. For more information, see Use Snowflake Columns Asset type and Use Snowflake Tags Asset type.
- Select the Masking action, which defines how data is masked. For more information, refer to Define Masking Instructions below.
- Select the Assets to mask (column or tag, depending on your selection).
- A single Masking Policy can be applied to one Asset column or to multiple Asset tags.
- Click Save.
To apply different masking rules for different roles, groups, or context conditions, use the same Vendor Policy Name across multiple PlainID Masking Policies on the same asset.
Ensure that all PlainID Policies referencing the same vendor policy ID use the same Signature Asset Type. Within that shared Asset Type, each ruleset may use different Asset Attributes as needed for its specific logic. Also, ensure that you keep the associated Asset/s consistent across all linked Column or Tag Asset Types.
Asset Types for Column-Level Requirements
To create a Column-based masking policy, ensure that your Asset Type/s meet the following requirements:
Table Mapping
To set Table Mapping:
- Ensure that "Is used for data filtering?" is enabled.
- Select Set Table Mapping to link your logical Asset Type with one or more physical Tables or Views in Snowflake, where the Masking Policy should apply.
- The mapping must include the fully qualified path to the table or view, following the format:
DB_NAME.SCHEMA_NAME.TABLE_NAME.
- The mapping must include the fully qualified path to the table or view, following the format:
Note: PlainID does not currently support ICEBERG Tables.
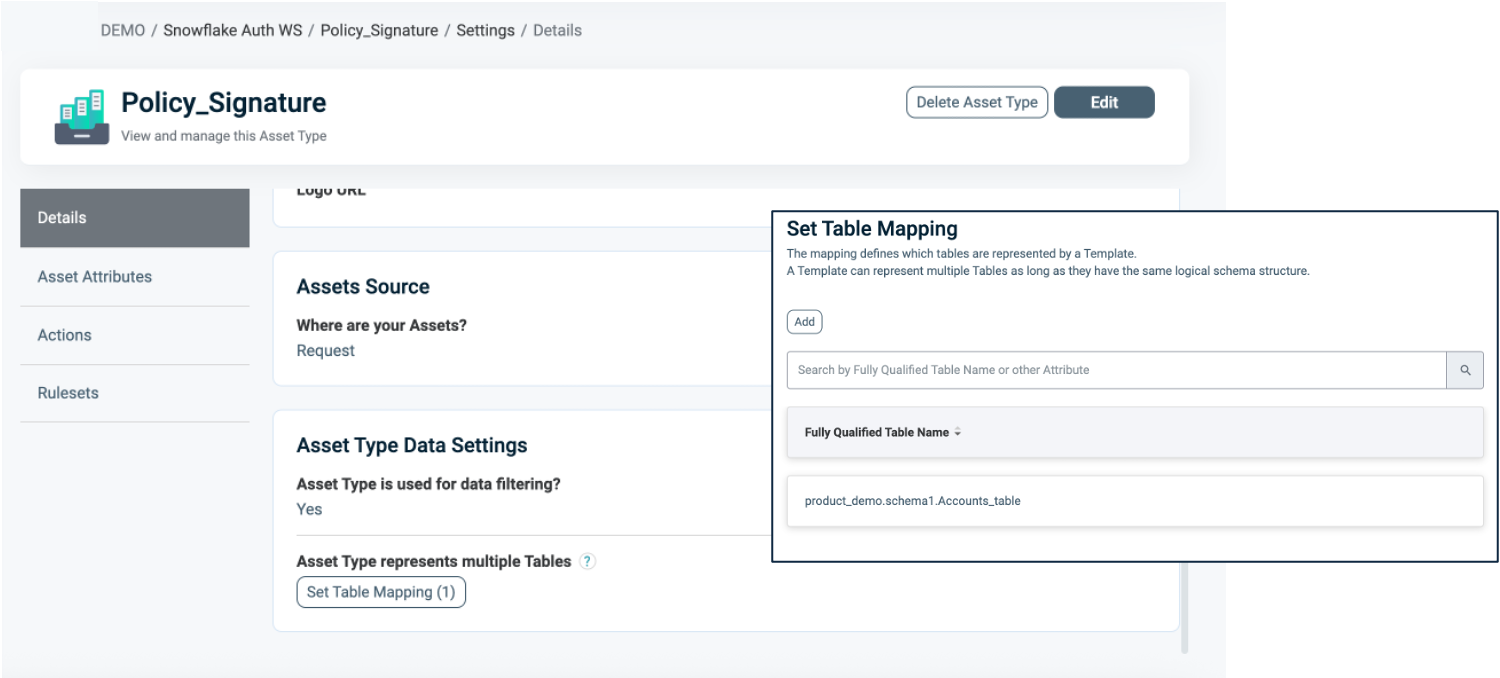
For more information about Table Mapping, refer to Dynamic Data Mapping.
Attribute Mapping
To set Attribute Mapping:
- Choose an existing Attribute or create a new one to use in your Masking logic.
- Refer to Managing Asset Attributes for more details.
- Define the data type (for example, String, Numeric).
- Enable Available for Policies = Yes. These attributes act as placeholders for filtering conditions.
- Click Set Data Column Mapping to map the logical Attributes to one or more physical Snowflake column/s.
- Note: Ensure the physical columns you wish to map are marked as "Use in masking = On" in the relevant Table or View in the Objects side panel. For more information, refer to Managing Columns for Masking.
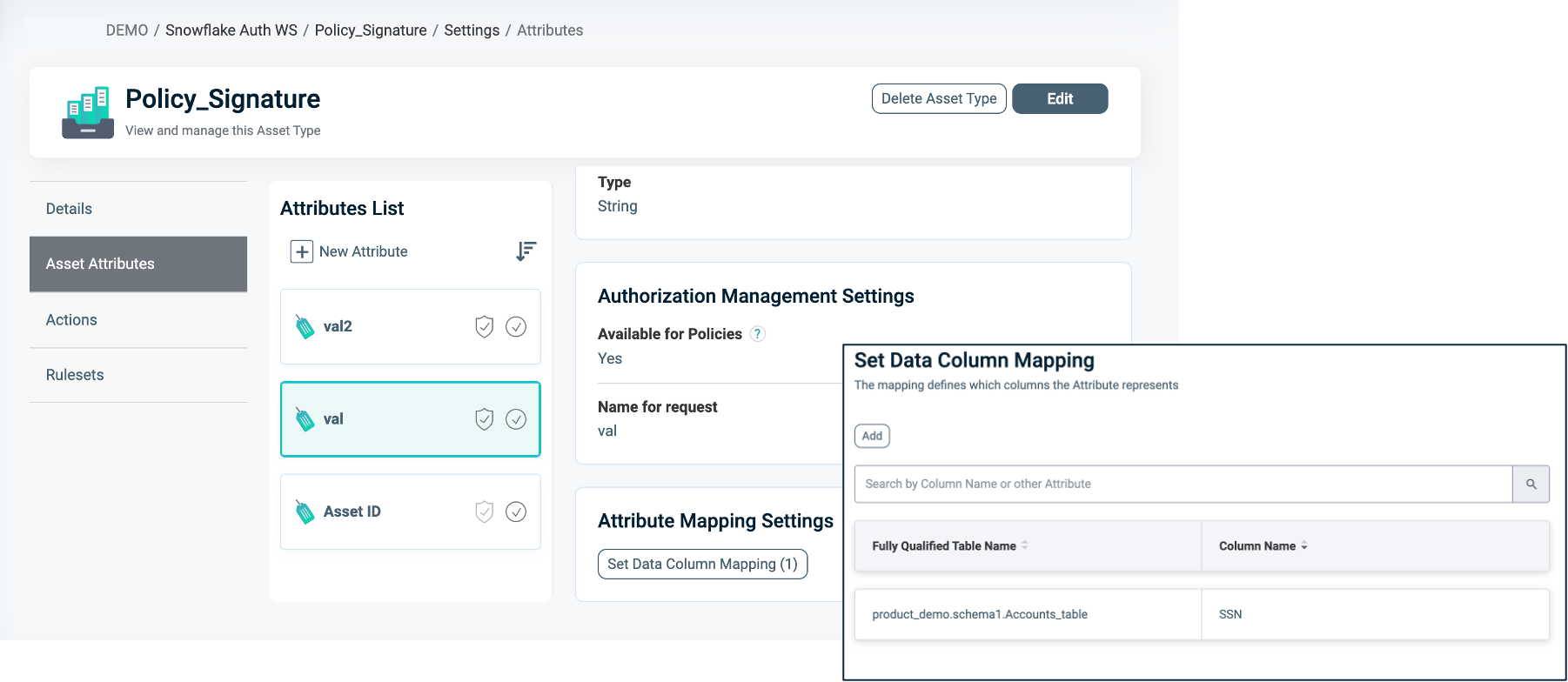
- Note: Ensure the physical columns you wish to map are marked as "Use in masking = On" in the relevant Table or View in the Objects side panel. For more information, refer to Managing Columns for Masking.
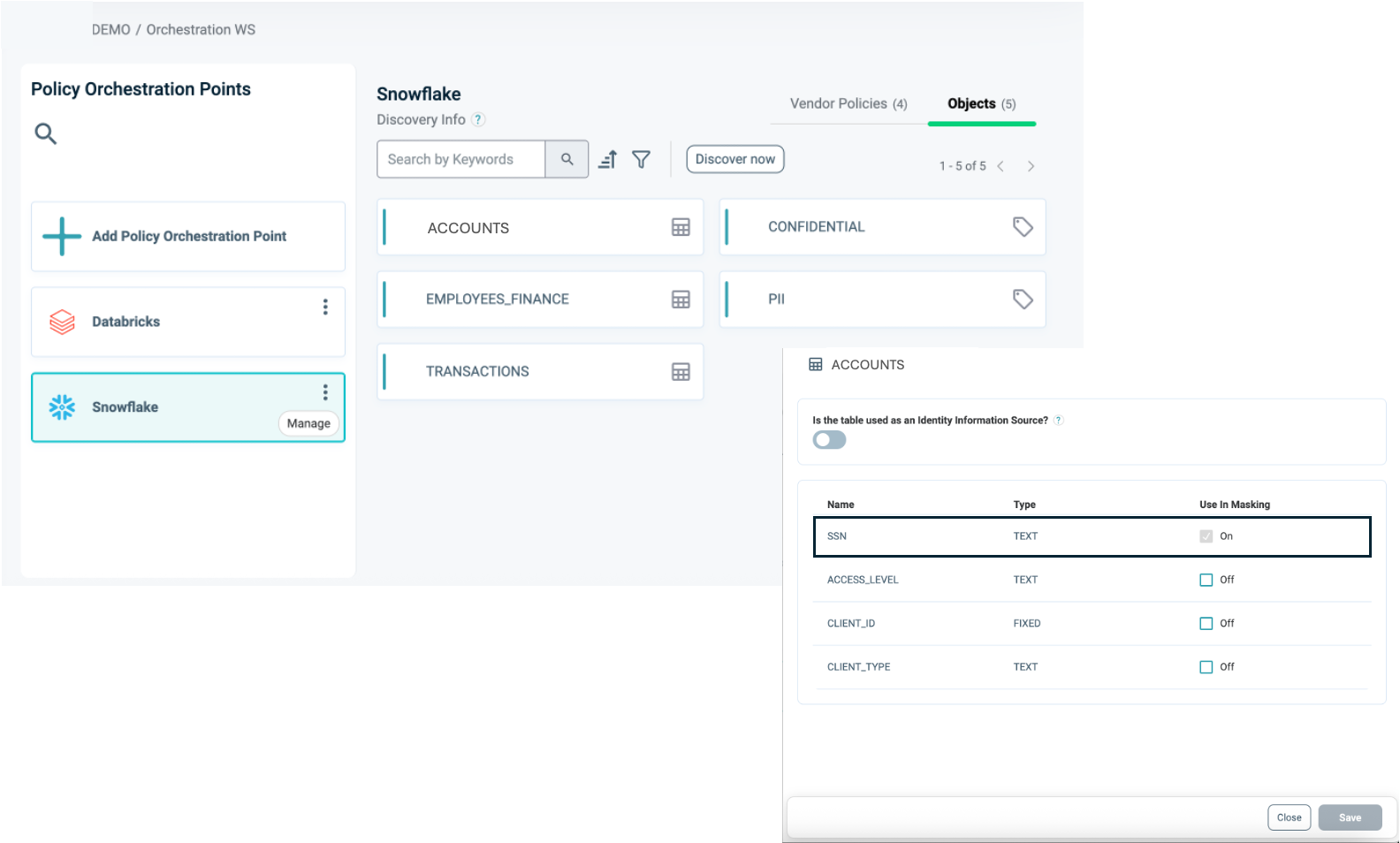
To connect an Asset Type with the Snowflake Application:
- Once the Asset Type is created, open the Snowflake Application in your Orchestration Workspace.
- Navigate to the Asset Types tab.
- Click Edit.
- Select the relevant Asset Types you want to associate with the Snowflake application.
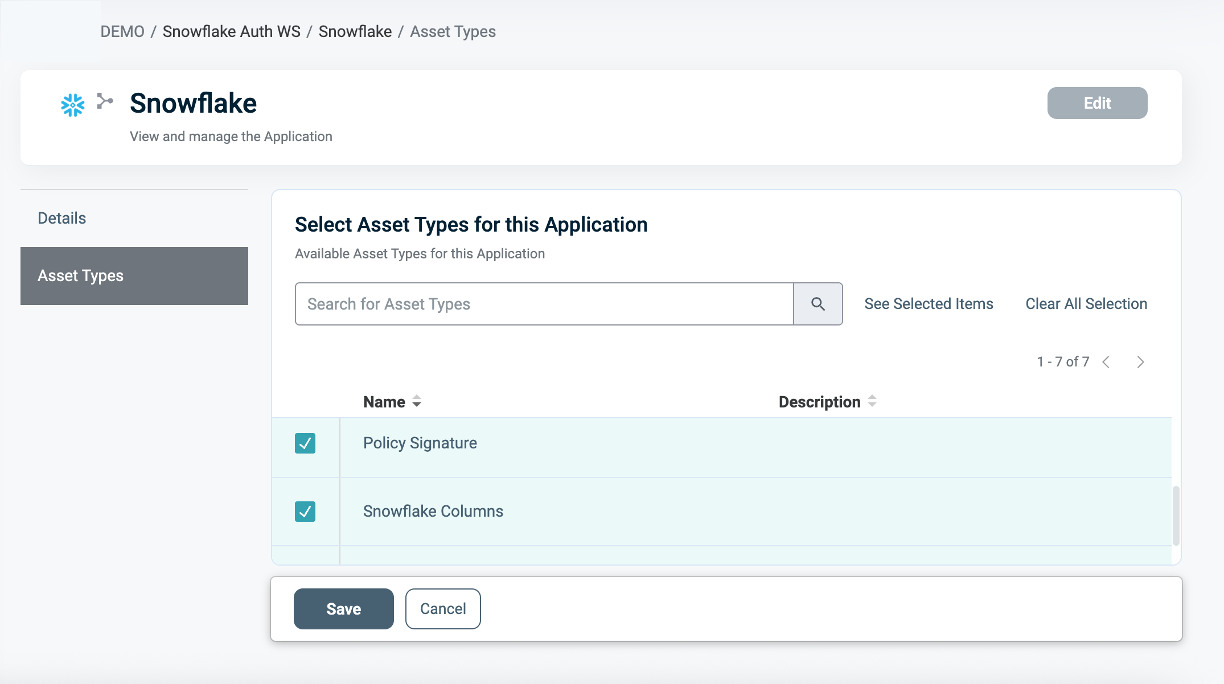
Defining a Ruleset for Masking Policies
To define a Ruleset:
- In the Asset type within the Ruleset tab, define the Masking logic using the Asset Attributes you created (for example,
Account_Level = 'Premium').
You can use Snowflake tables as an external Identity Source for contextual or dynamic rules (for example, Department = user.department). See our documentation on Managing Identity Source Tables for more information.
- Use PlainID's logic to combine operators (
=,!=,>,IN, etc.) with complex AND/OR relationships.
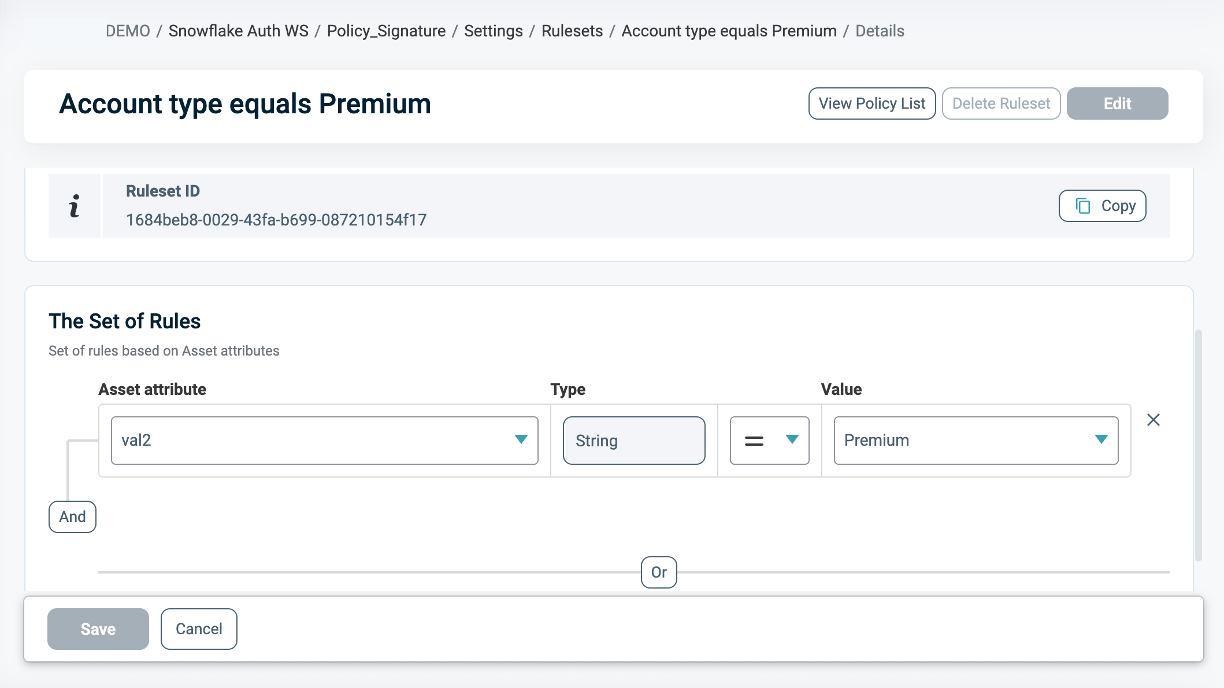
Snowflake Column Asset Types
The Snowflake Columns Asset Type is automatically generated when the Policy Orchestration Point (POP) is created. It represents a logical component that holds the available Snowflake columns for masking.
Snowflake Columns Assets
All those columns appear in the Assets section, and are either generated automatically from the Masking Policy in the Discovery process or created by the user. For more information on how to create new Assets, refer to Managing Columns for Masking.
In order to use Column Assets within a Masking Policy, the Signature Asset Type's Table Mapping must be predefined correctly. Refer to the Signature Asset Types for Column Level Requirements section for more information.
Snowflake Columns Actions
The Actions tab is used to define how the data should be masked. For more information, refer to Define Masking Instructions.
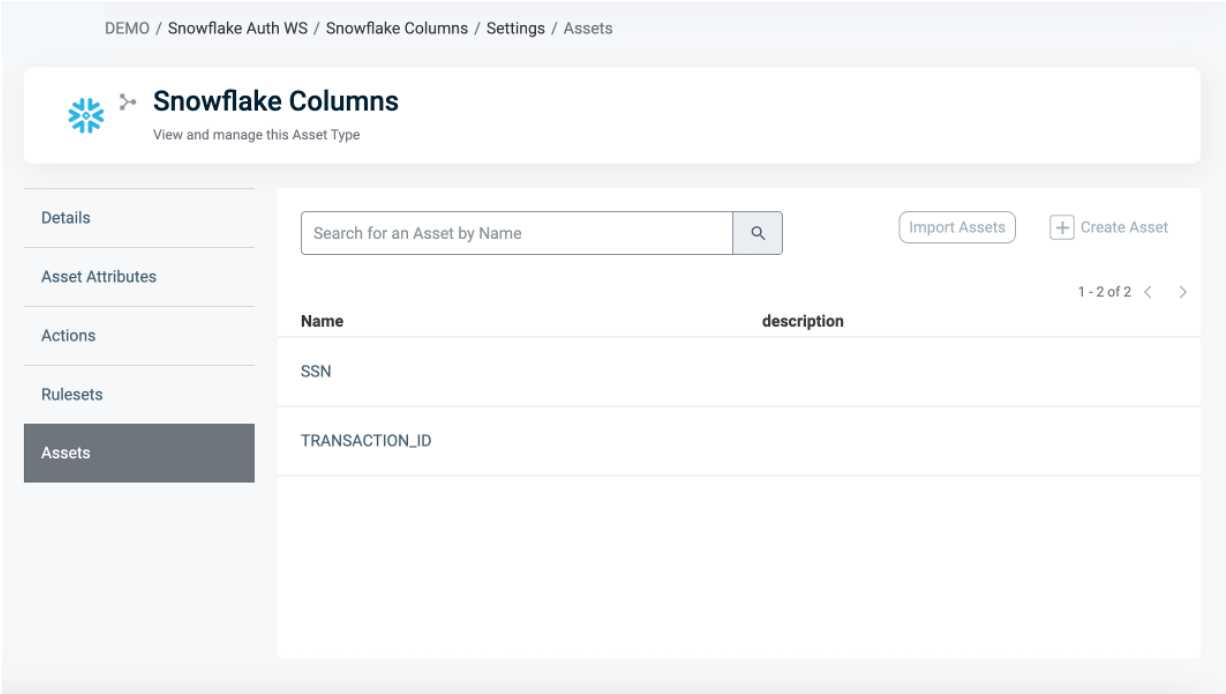
Asset Types for Tag Masking Policy Requirements
To create a Tag-based masking policy, ensure that your Asset Type/s meet the following requirements:
The Signature Asset Type contains the masking logic enforced by the Policy. To define that logic in your rulesets, create Asset Attributes that match the physical column names in the Snowflake tables where the tag is applied.
Example: to mask PII data, use conditional masking logic based on TYPE = 'Document', then create an Asset Attribute labelled TYPE that is identical to the TYPE column in your Snowflake table.
.png)
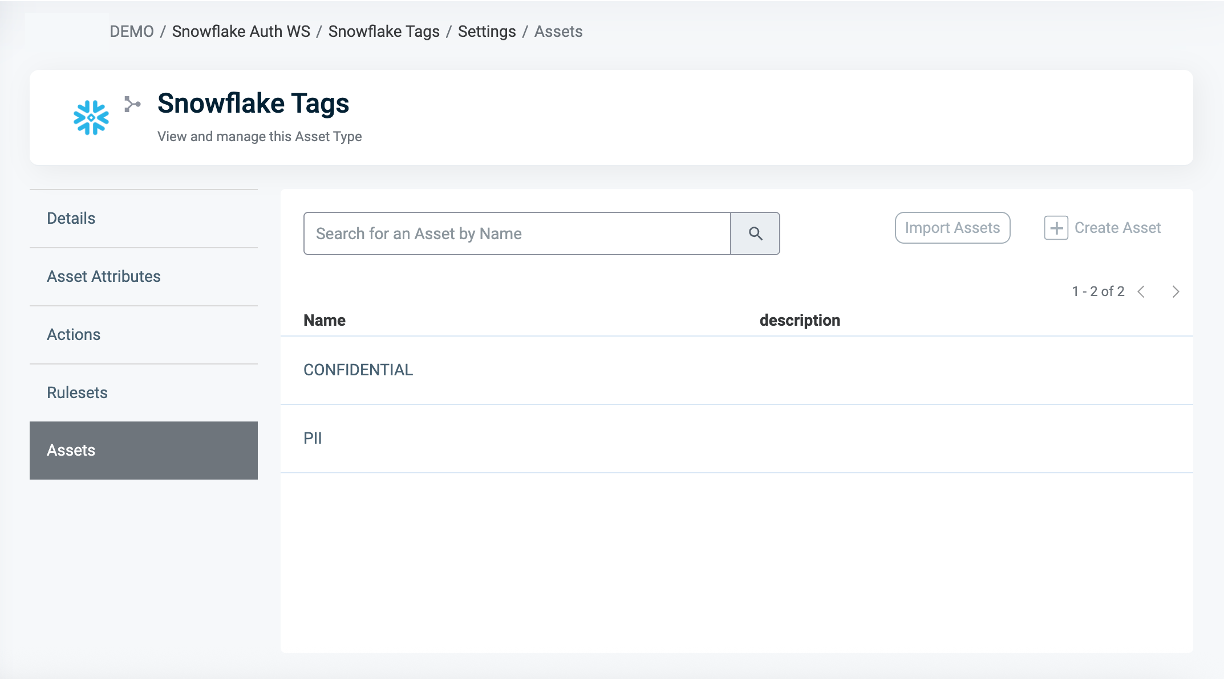
Snowflake Tags Asset type
Tag-based Masking Policies in Snowflake can be centrally managed through PlainID using the Snowflake Tags Asset Type. These Policies enable masking logic application based on Snowflake tags rather than on individual columns, supporting scalable and consistent data protection across multiple tables.
Snowflake Tags Assets
Available Tags to use in Policies related to Snowflake appear in the Assets section. PlainID discovers all available tags during the Discovery process and displays them in the Object Side Panel within the Orchestration Workspace.
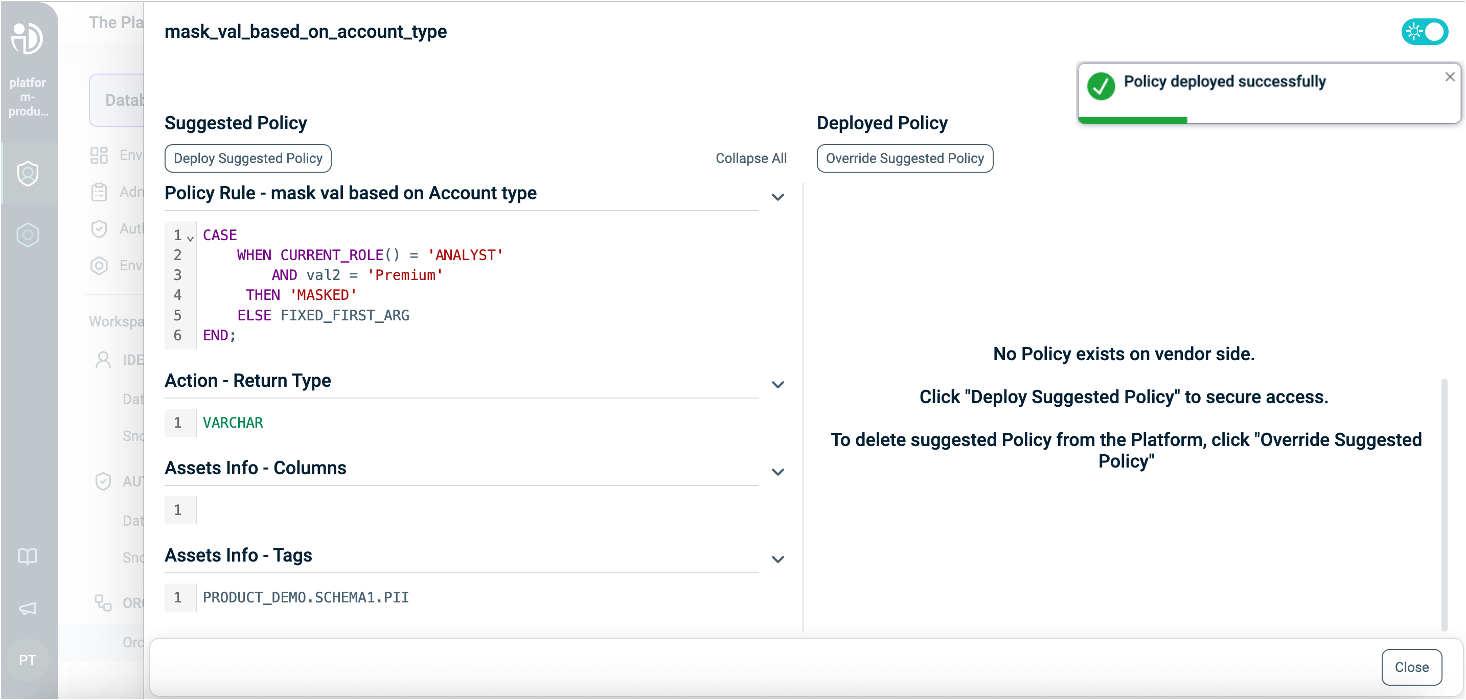
When you associate a tag with a Masking Policy, this tag is applied to your Policy through an argument called FIXED_FIRST_ARG. You can see this argument in the Policy Signature in the Policy Diff side panel.
This argument represents the physical columns' masked value, which is linked to the tag.
Note: PlainID does not create or manage Snowflake objects. Tags must be defined and applied to columns within the Snowflake environment.
.png)
Snowflake Tags Actions
The Actions tab is used to define how the data should be masked. For more information, refer to define Masking Instructions below.
Defining Masking Instructions
In the Snowflake Columns or Tags Asset Type, the Actions tab is used to define how the data should be masked. The masking instructions are applied to the selected Assets in your Policy.
You can either use a default masking instruction (e.g., Default for Varchar, Default for NUMBER) or create a custom masking instruction by specifying the following fields:
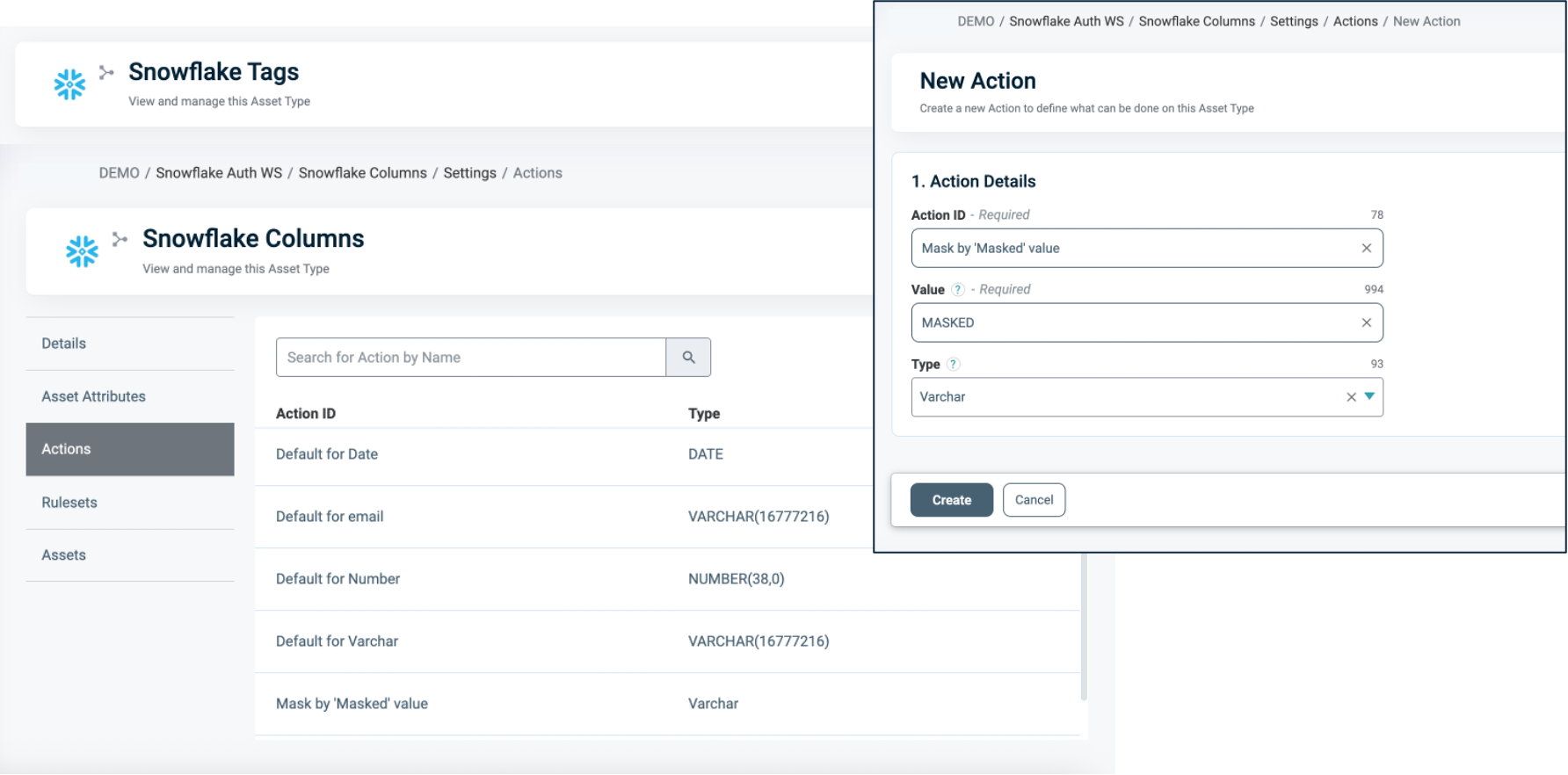
- Input an Action ID: The display name of the action.
- Input a Value: The actual masking logic (e.g.,
'MASKED'). - Choose a Type: The returned Masked Value's data type. This must match the RETURNS type declared in the Masking Policy (e.g.,
VARCHAR,NUMBER).
When Section
In the When section, you define the Conditions that provide contextual Identity data for your Policy, which determine when the Policy applies.
To define a Condition:
- Select an existing Condition or create a new one.
- A Policy can include multiple Conditions, combined with a logical AND operator, meaning all Conditions must be met in the Policy to grant user access. Ensure that you select Conditions from Identity Attributes linked to the POP's Identity Source.
- See Managing Conditions to learn how to create a new Identity Attribute Condition.
- Ensure that the Condition meets the Conditions for Masking Policy Requirements.
- Click Save.
Conditions for Masking Policy Requirements
- Only Conditions based on Identity Attributes are supported for use in Masking Policies.
- Ensure that an Identity Source table is defined within your Policy Orchestration Point (POP).
- Use an Identity Attribute that is mapped to one of the additional Identity Sources associated with the selected POP. For more details, refer to our documentation on Managing Identity Source Tables.
- Within a single Condition, you can only use Attributes from one Source.
Deploying the Policy
Once complete, navigate to the Orchestration Workspace and deploy the Policy to Snowflake.
Snowflake enforces the access decision based on the Masking logic defined in the PlainID platform.
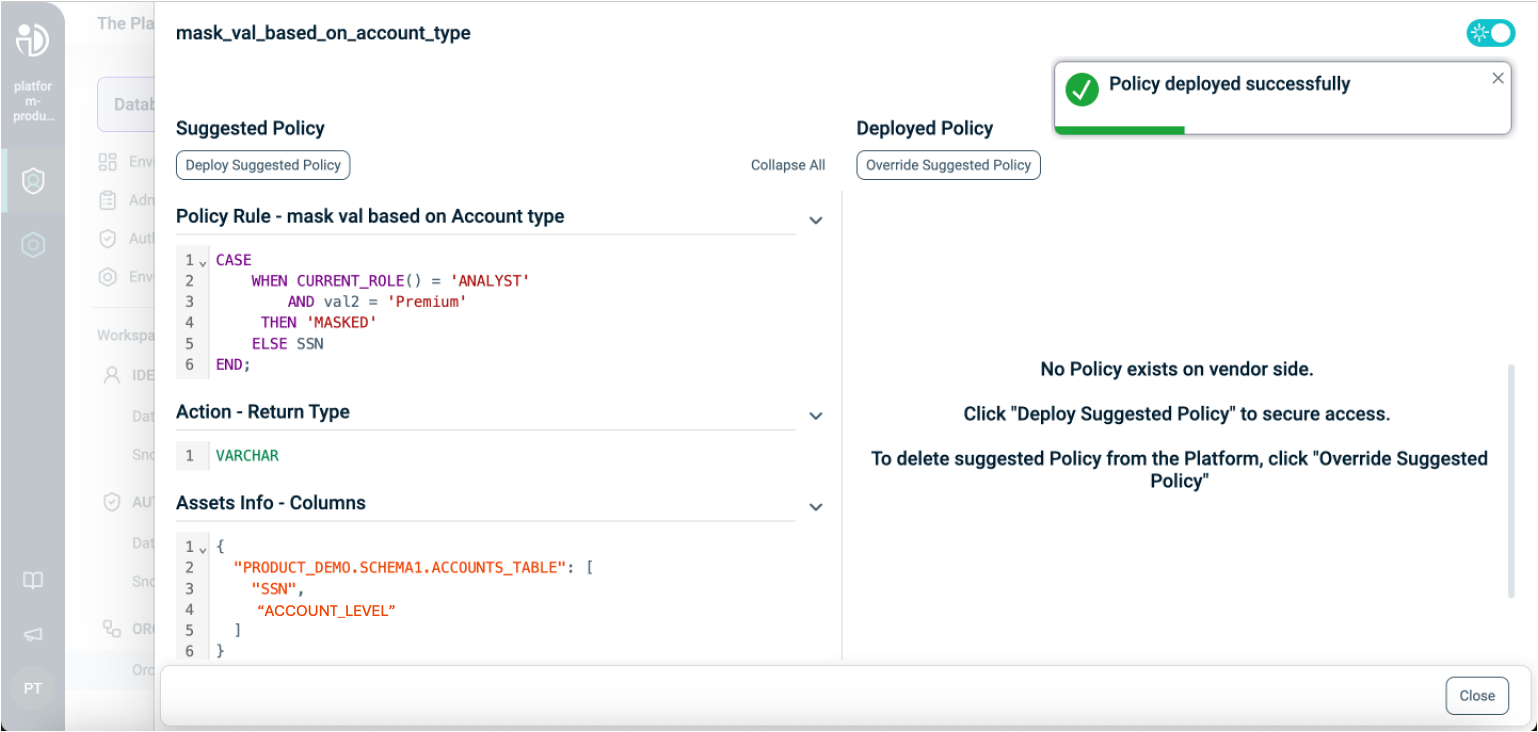
Column-Based Masking Policy Deployment:
Tag-Based Masking Policy Deployment:
Snowflake Masking Policy SQL Structure
This table explains the components of a Snowflake Masking Policy in SQL and compares them to their equivalents in PlainID, helping you translate and build your Policies easily within the PlainID platform.
Policy Syntax Table
| Snowflake terminology | Snowflake Syntax | Description | PlainID terminology |
|---|---|---|---|
| Policy Declaration | CREATE OR REPLACE MASKING POLICY <policy_name> |
Defines the Policy name and type (Masking Policy). Used to declare or replace an existing Masking Policy. | Vendor Policy Name, Vendor Policy Kind |
| Policy Signature | AS (VAL1 VARCHAR, VAL2 NUMBER..) RETURNS VARCHAR |
Declares the Policy's input arguments and return type. Arguments are used in the Policy masking logic. The return type of the Masking Policy must match the data type of its first argument. The first argument is the masked value. | Policy Signature mapped to Asset Type. Each argument that is used within the policy logic is created as an Asset Attribute. |
| Policy Logic | WHEN... |
Incorporates Snowflake identity functions: CURRENT_ROLE(), CURRENT_USER(), IS_ROLE_IN_SESSION(), CURRENT_SECONDARY_ROLES() to determine who should receive access in a given context. |
Dynamic group |
CASE... |
Use SQL expressions such as CASE statements to define the masking logic. | Policy logic uses the Policy arguments mapped into Rulesets, which can be dynamic (based on external identity data) or static (using fixed values). | |
EXISTS (SELECT... FROM... WHERE...) |
Use SQL subqueries with EXISTS SELECT for dynamic, context-based filtering. | Policy logic uses an external table mapped into conditions, where expressions typically compare attributes to static values. Note that a correlation must be defined using one of the Snowflake identity functions (e.g., CURRENT_ROLE(), CURRENT_USER(), IS_ROLE_IN_SESSION()). |
|
| Policy Output | THEN 'MASK' ELSE VAL1 |
Defines the instructions used for masking data. Based on the policy logic, the output can be the original column value, or a partially masked or fully masked version. The masking instructions are applied to the first argument. | Action in the Snowflake Tags/Columns Asset type. |
| Policy Application | Apply to a column: ALTER TABLE <table> MODIFY COLUMN <column> SET MASKING POLICY <policy> USING (<args>); Apply to a tag: ALTER TAG <tag> SET MASKING POLICY <policy>; |
Applies the Masking Policy to a specific column or tags. The same Policy can be reused across multiple columns, tables, or tags for consistent masking behavior. | The Column-based masking is defined in the Signature Asset Type Data Settings. The first column is the masked value, mapped as an Asset in the Columns Asset Type. The Tag-based masking is reflected as Assets in the Tag-Asset Type. |
Masking Policy Example
The following example demonstrates a Masking Policy that returns a 'MASKED' value for the Analyst role when the account_level is 'Premium'.
CREATE OR REPLACE MASKING POLICY MaskSSNForAnalystsOnPremium
AS (val STRING, val2 STRING)
RETURNS STRING ->
CASE
WHEN CURRENT_ROLE() = 'ANALYST' AND val2 = 'Premium'
THEN 'MASKED'
ELSE val
END;
ALTER TABLE Accounts_table
MODIFY COLUMN SSN
SET MASKING POLICY MaskSSNForAnalystsOnPremium
USING (SSN, Account_Level);
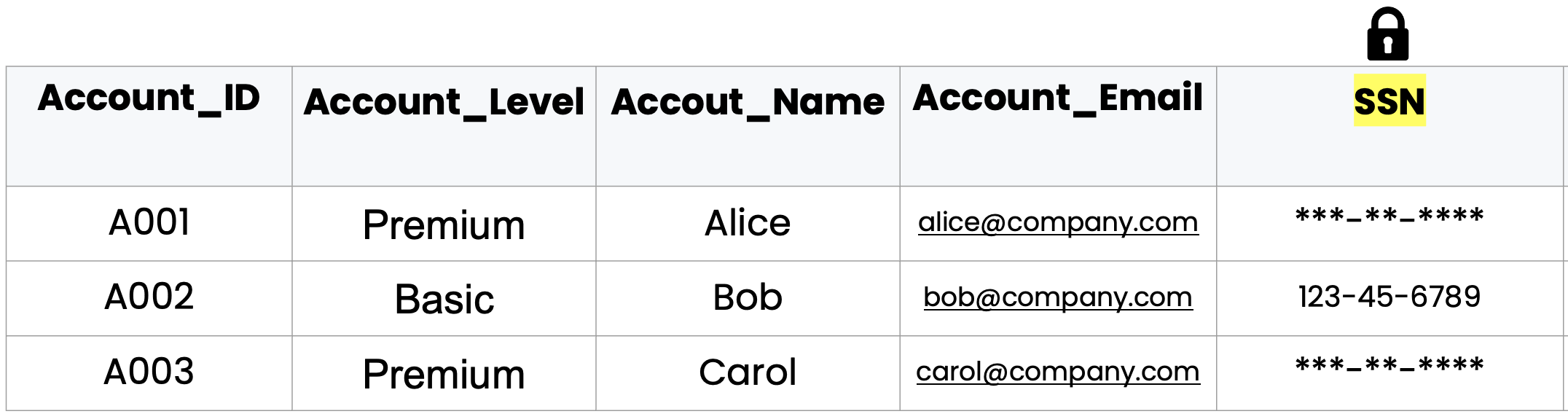
For the current role Analyst, the policy masks SSN values only for the Premium account level