Istio Sidecar
Istio is an open source, service mesh implementation that controls the communication to and between multiple service components. Istio is responsible for determining for example, which pods running service A can reach pods running service B.
Authorization Policies need to consider the Identities that are operating or wish to operate these services, and what they are trying to do. So, while Istio successfully supports the enforcement of access control policies, the question remains who is allowed, how and when and where this permissions is given or denied.
The Istio Authorizer runs on the Istio Service Mesh, delivering high performance as it enforces/authorizes the Organization's Access Policies. The PlainID Sidecar supports the Istio Service Mesh.
Istio Sidecar Installation
It is recommended that you use Helm Chart v3.8.0 to install and configure a Sidecar solution on Kubernetes.
When installing and using an Istio Sidecar Authorizer, it is recommended that you install and configure the Sidecar solution on Kubernetes using Helm Chart. For more information on downloading and configuring Istio, see the Helm Chart in the Admin Portal.
In addition to running the Sidecar itself, the Helm Chart is responsible for installing and configuring the Sidecar to integrate with other components. Helm v 3.8.0 is required to properly install and configure the Sidecar solution with your Kubernetes cluster.
Prerequisites
The following applications are required to install and configure Istio for use with the Platform:
- Kubernetes 1.15+
- Istio 1.15
- Helm 3.8.0+
Obtaining the Authorizer Package/Bundle:
- For PlainID v.4.x: Contact PlainID Tech Support to request the Istio Authorizer download package.
- For the Platform v5.x: contact our Technical Support team for the Authorizer Deployment Download.
The Policy Authorizer Package Content
| File | Description | Should be updated |
|---|---|---|
| /plainid-sidecar/templates/crds.yaml | K8s Custom Resource Definitions | No |
| /plainid-sidecar/templates/manager.yaml | Deployment configuration for authz-operator (plainid-controller-manager) | No |
| /plainid-sidecar/templates/namespace.yaml | Deployment configuration for authz-operator (plainid-controller-manager) | Optional |
| /plainid-sidecar/templates/rbac.yam | K8s Namespace configuration for authz-operator (plainid-controller-manager) | Optional |
| /plainid-sidecar/templates/serviceAccount.yaml | K8s Service Account configuration | Optional |
| /plainid-sidecar/templates/webhook.yaml | PlainID Mutating Webhook configuration | No |
| /plainid-sidecar/Chart.yaml | Contains information about the Helm Chart | Yes |
| /plainid-sidecar/filter.yaml | Envoy configuration example (EnvoyFilter kind) | Yes |
| /plainid-sidecar/values.yaml | The default configuration values for this chart (AuthZ Operator and Sidecar settings) | Yes |
| /samples/authz_v1_plainidinjector.yaml | AuthZ Sidecar Pod-Injection configuration | No |
| /samples/sidecar-echo.yaml | AuthZ Sidecar configuration example with settings | Yes |
| /images.txt | List of PlainID AuthZ Operator and Sidecar images with tags (versions) | No |
Usage Example
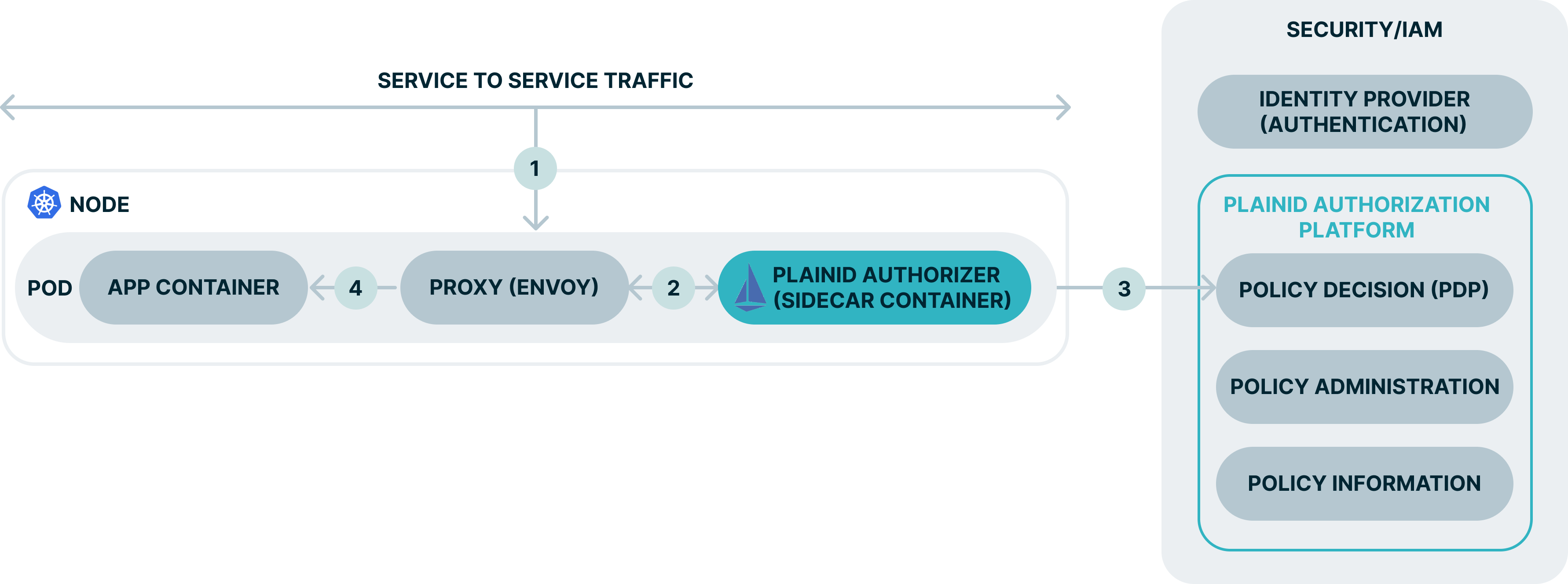
Explanation
- The client sends its access/ID token in the request header.
- The request is intercepted by the Envoy Proxy and passed to the PlainID Sidecar container. The PlainID sidecar container is automatically injected into the pods through configuration settings within Istio.
- The PlainID sidecar container requests an access decision from the PlainID PDP which responds with a dynamically calculated access decision based on the policies configured within the PlainID Authorization Platform. The decision can be on the request URL, request header, and request body.
- In case the authorization decision is Permit, the Envoy proxy passes the request to the service container as-is or Enrich the request header with entitlements or additional information to provide specific access data to the service. Otherwise, If the authorization decision is denied, the request never reaches the actual service container and a 403 response is returned immediately.