With the API Access Authorization Pattern, PlainID Authorizers add an enforcement point in the flow of applications and services communicating over REST requests. By integrating into API Gateways, Proxies, and Service Meshes, PlainID Authorizers can intercept API REST requests and dynamically determine whether they are allowed based on the calling identity context or should be blocked as unauthorized/forbidden.
API Access Authorizers seamlessly integrate your existing gateway systems with PlainID's dynamic authorization calculation, adding access control directly at the API gateway. This centralized enforcement ensures robust, consistent security policies, streamlines access management, and enhances the overall security posture of your applications.
How does it work?
When standard REST traffic passes through the API gateway, it is routed through the PlainID Authorizer to initiate a dynamic authorization check. The API Access Authorizer translates the incoming REST requests and sends them for evaluation in PlainID’s Policy Decision Point (PDP). The API Access proxy in the PDP uses predefined API mappers to form a standard access decision request based on the intercepted REST request at the gateway level. This structured request is processed by the PDP, which evaluates the request and returns a Permit/Deny result to the Authorizer. The Authorizer then either allows the original REST request or returns an unauthorized response to the requester.
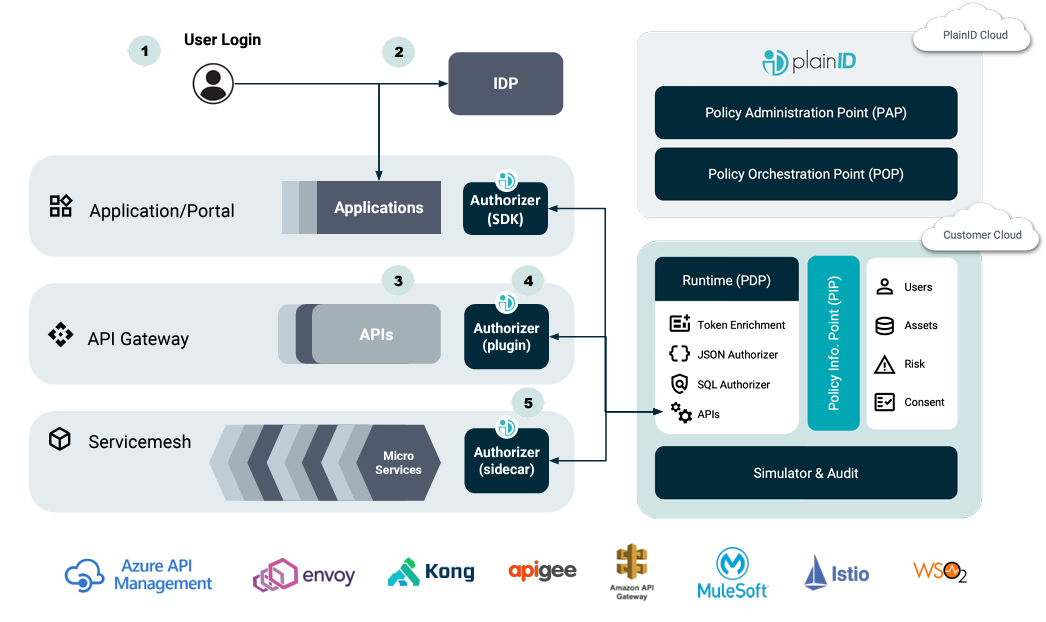
1) User logs into the application
2) Application sends authentication request to the Identity Provider (IdP)
3) The application sends API calls directed through the API Gateway to access different services
4) PlainID’s Authorizer (implemented as a plugin in the API Gateway) receives the request and makes a dynamic access decision in real-time, based on the Policies. The decision can permit/deny the transaction OR equip the transaction with token exchange/ enrichment for additional identity-aware permissions.
5) The API call is passed on to the service layer
This approach significantly reduces the load on the application, minimizes development effort, and enables easy integration and quick enforcement using the PlainID solution. With the API Access Authorization Pattern, PlainID Authorizers add an enforcement point on a generic common flow of applications and services communicating over REST requests. By integrating into API Gateways, Proxies, and Service Meshes, PlainID Authorizers can intercept API REST requests and dynamically calculate if they are allowed for the calling identity context or should be blocked as unauthorized/forbidden.
API Access Authorizers seamlessly integrate your existing GW systems with PlainID’s dynamic authorization calculation and add access control directly at the API gateway. This centralized enforcement ensures robust, consistent security policies, streamlines access management, and enhances the overall security posture of your applications.
Service Mesh Authorization Pattern
Service meshes manage communication between microservices in a distributed architecture. Similar to the API GW pattern, PlainID's Service Mesh Authorizers enhance authorization capabilities within a microservices architecture by ensuring the integrity of service-to-service communication and enforcing fine-grained access control policies.
Supported Service Mesh Authorizers
- Envoy
- Istio
Using API Mappers
PlainID offers the capability to define API matchers and mappers, allowing easier management of your API ecosystem and securing a wide range of services and routes with dynamic authorization. These enforcement patterns help define different access controls for various services in your ecosystem. By doing so, your sensitive data and protected resources are secured at the API access level. Mappers will also help describe the business assets to be protected and how they should be extracted from different REST API requests across various services.
For detailed usage instructions, please refer to the Managing API Mappers documentation.
Example API Access Control Use Case Scenario
Securing Digital Services with API Authorization: A company aims to secure its digital services by implementing a robust API authorization framework. The company serves a diverse user base, including employees and customers, each associated with various data attributes (e.g., user profiles, account data, and other sensitive information) that determine their access levels.
PlainID efficiently matches these attributes with service request data to enforce access control policies. When a user attempts to access a specific service (e.g., a "User-Dashboard" service), the request is evaluated by the Policy Decision Point (PDP), which checks the relevant policies. These policies validate the user's identity data against the service request, ensuring that only authorized users can access the specified service.
The PDP dynamically assesses the required identity attributes based on the specific service being accessed, while PlainID secures the digital service and ensures it safeguards the underlying data.
Supported API Access Authorizers
The Authorization Platform supports several different Authorizers.
Contact PlainID for more information on these Authorizers, or visit our Integration Hub for additional details on each of our PlainID Authorizers.