With the Token Enrichment Authorization Pattern, PlainID Authorizers dynamically enrich user authorizations by calculating custom entitlements or claims based on policies, which are then served to consuming services.
IDP Authorizers help you seamlessly integrate your existing IDP systems with the Platform's dynamic Authorization calculation. This integration enables you to define fine-grained Authorization Policies, enforce access rules, and manage user privileges across your entire IDP ecosystem by enriching user claims during the user's authentication journey.
The IDP Authorizer integrates the IDP authentication flow with the PlainID Token Enrichment Service, establishing a connection and initiating a request for Policy-based, real-time calculated user claims by PlainID’s PDP, which are then included in the user’s token during generation by the IDP.
This process allows applications and services that rely on user token claims for access management to seamlessly benefit from the dynamic enrichment of claims provided by PlainID during the authentication flow.
Use-case Example
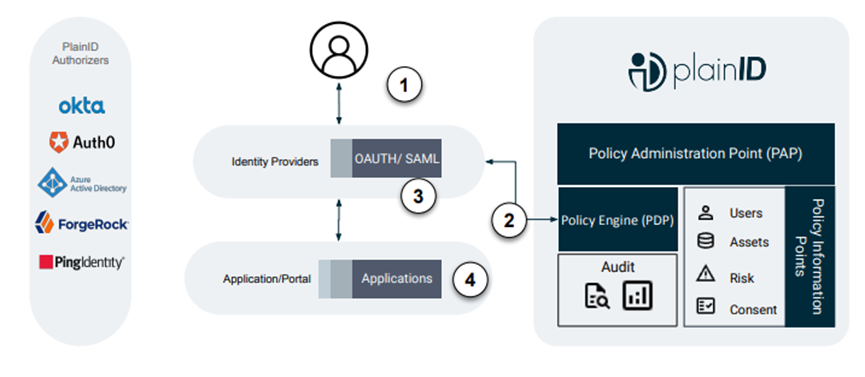
Explanation
- User Authenticates to the IDP.
- IDP calls out to PlainID to request which claims the user is authorized to have.
- PlainID real time calculated claims added by the IDP and enriches the user token.
- IDP signs the JWT and it is provided to the application.
An additional enrichment flow supported by other PlainID Authorizers can leverage PlainID's dynamic authorization capabilities. These authorizers calculate entitlements based on policies to enrich service API requests, which are then used by customer services during internal authorization enforcement.
How Token Enrichment Works
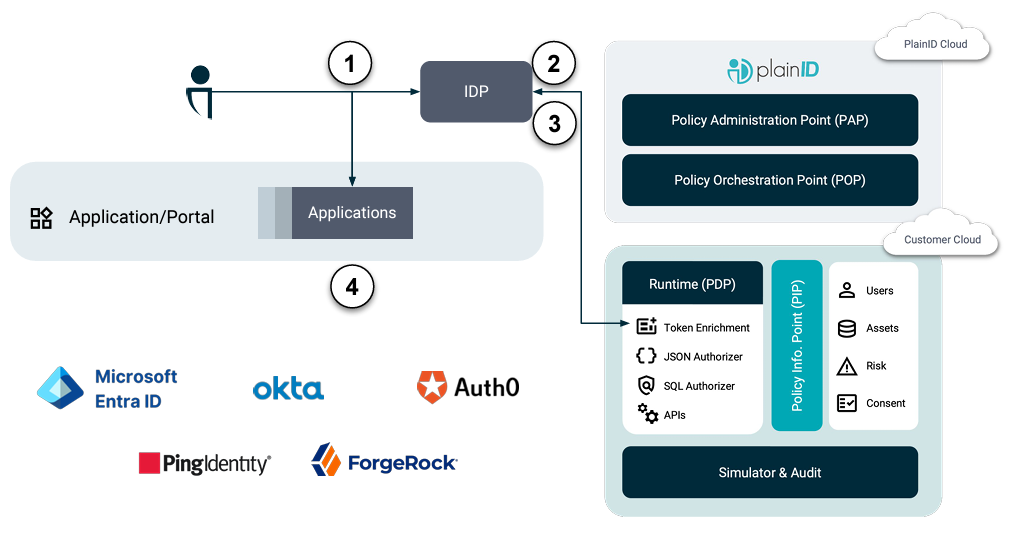
- User Authenticates to the IDP
- IDP calls out to PlainID and request which claims and claims values the user is authorized to have.
- Claims are added to the JWT
- JWT is signed and provided to the Application.
Token Enrichment Authorizers
PlainID offers the following Token Enrichment Authorizers:
Contact PlainID for more on these Authorizers and visit our Integration Hub for more information on each of our PlainID Authorizers.
Check out our PlainID Token Enrichment Service article for more information.