With the Data Access Authorization Pattern, PlainID Authorizers dynamically enforce access to data. Data Access Authorizers, help you seamlessly integrate your existing Data Gateways, Data Access Layers and Data Services with PlainID’s dynamic authorization calculation.
This integration enables you to define fine-grained authorization policies, and enforce access rules both on records access and for masking of properties.
Data Access Authorizers usually leverage PlainID’s PDP Policy Resolution to get calculated access for records and properties and enforce the data access by applying this resolution.
The Data Access Authorizers assist with enforcement at the data level in one of the following ways:
- Intercept data queries and apply dynamically calculated filters on them
- Apply filtering of records and properties after data was already fetched from a data service
- Guide a data service for the required enforcement by enriching its service request with the policy resolution
With query modification or data filtering the data services are seamlessly integrated with dynamic authorization and users will get only permitted data according to identity context, data policies and masking instructions, allowing to tighten your data regulation and yet keep them robust and dynamic.
About Query Modification
The PlainID Data Access Authorizer is integrated into your data solution or data layer with one of the supported technologies.
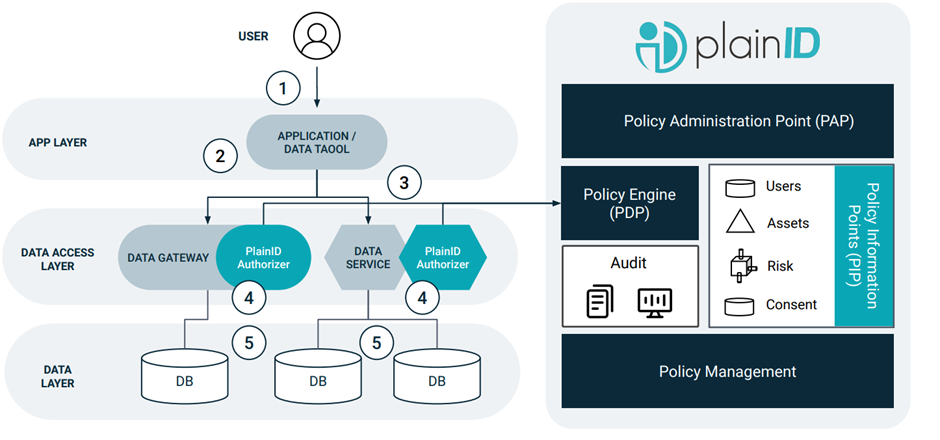
- The user logs into the application or data tool
- The application makes an access request to the data through a PlainID Authorizer for a Data Gateway or Data Service (e.g. sidecar or plugin, respectively – SDKs are also available to support other data technologies)
- The PlainID Authorizer queries PlainID’s PDP for a dynamically calculated Authorization resolution
- The response is translated to a data filtering clause for query modification
- The original query is modified based on the Authorization resolution through data filtering or masking of the columns/rows/cells
Current Query Modification Authorizers include:
Two additional data enforcement pattern are possible by integrating Authorizers to your data service:
-
Filtering data service responses - PlainID Authorizer will process your data service response, after data was fetched from data sources. This processing will include filtering our records objects and/or mask object properties.
Currently available with PlainID JSON Masking Authorizer
-
Enriching data service request - PlainID Authorizer will enrich your data service request with headers containing instructions for the required data filtering and your service will enforce these instructions as part of its logic.
Currently available with PlainID Istio Authorizer
Data Policy Authoring and Data Mapper Usage
To assist with policy authoring designed for data access management, PlainID allows to set up Asset Types used for data filtering. In addition, policies can be defined using a combination of asset types representing row level and column level access rules and use the relation derived from the policy to make accurate data access enforcement.
Together with these capabilities Data Mappers can also be leveraged to smartly map your physical data ecosystem to the logical business representation on which you will manage your policies centrally.