Overview
PlainID’s SQL Database Authorizer is a service designed to enhance data security and enforce policy-based access control within SQL databases. It intercepts SQL queries—whether sent directly from an application or through PlainID’s SQL Libraries—and dynamically modifies them based on PlainID Policies.
By evaluating each query at runtime, the Authorizer ensures users only access data they are explicitly authorized to view. This includes support for fine-grained controls at the row, column, and even cell level, making it ideal for environments handling highly sensitive information.
The Authorizer integrates seamlessly with popular databases such as PostgreSQL and Microsoft SQL Server, and works across a variety of technology stacks including J
ava Spring Boot and .NET. It supports standard SQL clauses (SELECT, FROM, WHERE), as well as more complex queries involving JOIN and WITH statements—ensuring broad compatibility without requiring application-side query rewrites.
This approach guarantees data integrity, enforces organizational access policies, and helps maintain compliance with data protection requirements in a flexible, scalable manner.
Note: If using different SQL statements or query options, consult with PlainID Support for support or required enhancements.
Note: The legacy BigQuery Authorizer remains supported for backward compatibility. However, all future enhancements will be exclusive to the SQL Authorizer.
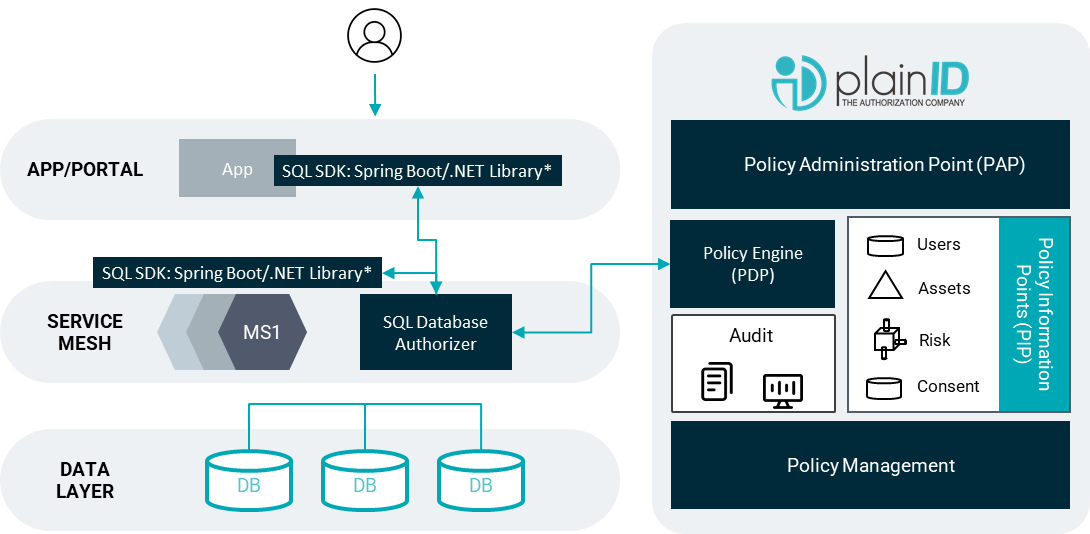
- Users navigate to an application to interact with digital assets.
- The PlainID library (Java Spring Boot or .NET SDK) is initialized in either the application layer or the microservice responsible for fetching data from the database.
Those libraries initiate a call to the PlainID SQL Database Authorizer REST API. - The SQL Database Authorizer examines the original SQL statement intended for use by the microservice or app (like
SELECT * FROM CLIENTS_TABLE).
The SQL Database Authorizer then communicates with the PlainID Policy Decision Point (PDP) REST API to obtain an authorization decision, performed in the context of the user's identity. - Based on PlainID's PDP access response, the Authorizer then modifies the original SQL statement. It transforms the statement to align with the authorized access, generating a new SQL statement. For instance, it may change the statement to something like
SELECT FNAME, LNAME, ADDRESS from CLIENTS_TABLE where CLIENTS_TABLE.REGION=’US’. - Finally, if authorized, the appropriate data is fetched from the database.
Patterns and Implementation
Before implementing Policies on your SQL queries, it's important to understand how the SQL Authorizer is deployed, how it integrates with your systems, and how it enforces Policies at runtime. The following articles provide everything you need to get started—from setup to execution:
Deployment and Integration Patterns
- Deployment Guide: Learn how to deploy the SQL Authorizer using supported methods like Helm and Docker across different environments.
- Integration Patterns: Explore how to interact with the Authorizer via REST API or SDKs.
Policy Implementation
- Policy Implementation: Understand how SQL Queries work with Policies, including capabilities like filtering and masking.