For SaaS Authorization Management, PlainID offers an Authorizer integration pattern for this third-party vendor. For more information, see SaaS Authorization Management.
The Zscaler Authorizer centralizes policy management for Zscaler Private Access™ (ZPA) and industry-leading SaaS applications and tools.
Using the Platform with ZPA enables you to:
- Streamline access to endpoint: providing centralized and automated policy management with reduced manual efforts that are currently required across Zscaler and the ecosystem.
- Minimize security gaps: Ensure that ZPA policies are consistently applied across the enterprise using the Policy-Based Access Control (PBAC) framework.
- Gain visibility and the ability to monitor policies: from a single dashboard you can visually see Policy components, see the Policy as code, review, modify, and reconcile any discrepancies between ZPA policies and the mapped Policies managed in the Platform.
- Adapt to evolving requirements: by easily updating Policies as needed and deploying modified Policies back to ZPA as needed.
About Zscaler Private Access™ (ZPA)
ZPA is a cloud-based service that provides secure access to internal applications by creating secure, direct connections between authorized users and specific applications, regardless of their location, using a zero-trust architecture that verifies every access request.
ZPA focuses on cloud security, including protection against ransomware and threat protection. ZPA provides role-based access control to the organization's application segments and application groups. Specific access policy rules are applied within Zscaler on a top-down, first-match principle.
In ZPA, an Application is an FQDN (fully defined domain name), local domain name, or IP address.
Each application is defined as part of an Application Segment, which is a logical set of applications grouped based on access type (for example, restrict access for all applications).
Application Segment Groups group together numerous application segments, allowing the configuration of user access policies to a wider number of applications. Application Segment Groups enable you to apply changes more widely as well. For more information, see Zscaler Policies and Objects
ZPA Authorizer Workflow
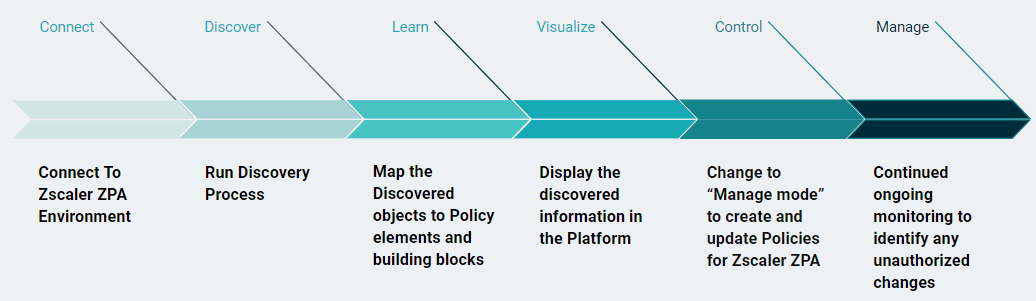
The workflow for the ZPA Authorizer includes:
- Connecting to the ZPA Environment
- Running the Discovery Process
- Working in Learn Mode
- Working in Managed Mode
You can switch between Learn and Managed modes in the Orchestration Workspace. For more information, see Learn and Managed Modes
Connecting to ZPA
After configuring a Zscaler POP to connect to a ZPA Environment, in initial discovery is triggered. Connecting to a ZPA Environment involves defining the integration parameters between the SaaS Authorization Management and ZPA (see Managing a Zscaler Policy Orchestration Point) and adding the relevant credentials.
Run the Discovery Process
A discovery process can be initiated at any time by clicking the Discover Now button in the Orchestration Workspace. As explained above, the initial discovery is automatically initiated with the creation of the first Zscaler POP). During this process, the Platform will identify the IDP logo and name, as well as:
- IDP Attributes that are used in Policies. Note that ZPA can have multiple IDPs. Each IDP will be mapping to a separate Identity Workspace. Within the ZPA and also use vendor-specific Attributes that will be defined during the Discovery as an AUX for the specific POP in which the Discovery took place. For more information, see Mapping Identity Attribute Parameters.
- Additional sources needed to create Identity Attributes in the Platform, per IDP and mapped in the Platform to the expected Identity Workspace.
- Identity-related values used to build Dynamic Groups.
- Additional objects that are mapped to objects in the Policy elements. For example, included in the discovery and mapping stages are the creation of Asset Templates, Identity Templates, Attributes and more.
Working in Learn Mode
In Learn mode, you can see the discovered objects that are mapped to Platform Policies and objects, seeing a visual representation of the ZPA Policies and objects in each of the Platform Workspaces.
Working in Managed Mode
Once the Learn mode is complete, it is possible to begin using the Zscaler Authorizer in Managed mode. The Managed mode allows you to begin updating existing Policies, creating new Policies which can then be deployed back to ZPA for enforcement, deleting Policies etc.
The Manage Mode includes:
Manage: Creating, update, and delete Policies in ZPA.
Enforce: Enforce access in ZPA based on managed Polices in the Platform.
Monitor: Continue ongoing monitoring to identify any changes in the ZPA environment and alert any changes made in the Platform by showing a discrepancy between the Suggested Policy (in the Platform) and the Deployed Policy (in ZPA).
Mapping Zscaler Objects
During the Discovery Process, the following ZPA objects are mapped to Platform objects:
| ZPA Objects | Mapped Platform Object |
|---|---|
| IDP | ZPA can have multiple IDPs. Note: If multiple IDPs are defined, the one with the enabled scheme is selected. If more than one scheme-enabled IDP exists, one will be automatically selected. |
| Application Segment | Asset: Each Application Segment is mapped as an Asset and managed internally |
| Application Segment group | Asset: Segment groups provide the following benefits and enable you to: - Logically group Application Segments together for easier management. - Provide a layer of abstraction to simplify access policy configuration/ |
| Conditions | Conditions in Zscaler provide environment and access-related information that influence that access of a user as part of a policy. They are mapped to Platform Conditions. |
| ruleOrder | Each Policy in Zscaler has a number of Attributes that are mapped to the Platform. The ruleOrder parameter in Zscaler is included in the structured Rego code displayed in the Orchestration Workspace when you click on the Policy. It is also displayed on the Policy tile on the Vendor Policies tab, indicating the order in which each Vendor Policy is evaluated when determining the access decision. |