Installation
- Under your Trino installation, navigate to the plugin folder.
- Create a folder with the name: plainid
- Copy the following .jar files to the new folder:
- trino-plainid-1.0-SNAPSHOT-jar-with-dependencies.jar
- plainid-commons-4.6-SNAPSHOT-jar-with-dependencies.jar
Configuration
To configure the Trino Authorizer:
1. Under the trino/etc folder create a file with the name access-control.properties
2. Edit the file by adding the following values (explanation below):
access-control.name=plainid
plainid.u**rl=https://
3. After completing the installation and configuration of the Trino plugin, restart Trino.
4. Check the Trino logs to verify that the PlainID plugin was loaded properly:
INFO main io.trino.security.AccessControlManager
-- Loaded system access control plainid --
The plugin relies on the Identity being sent in the connection extraCredentials property:
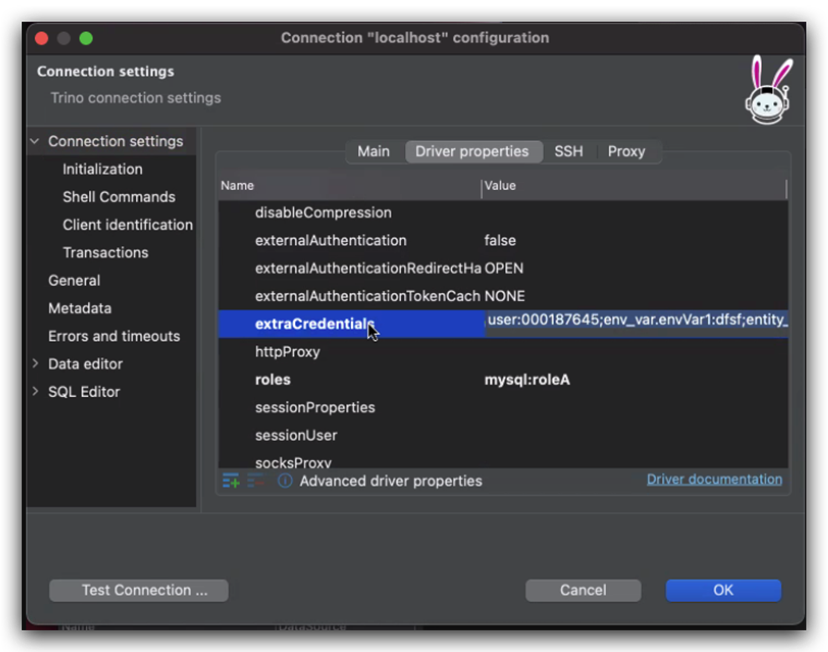
5. Your querying Application should inject the user ID making the query to the connection in the form of
6. For testing purposes, you can set this property in the driver configuration of your SQL client Application.
7. Additional parameters can also be sent in the extraCredentialsproperty.
Aside from the user that is parsed according to the userFieldconfig key, other key-value pairs in the extraCredentials are parsed according to the two prefix config keys and divided to Environment Variables and Entity Attributes sent in the runtime request in this form.
{
entityAttributes: {
key: [
value
]
},
environment: {
key: [
value
]
}
}
Parameter Explanation
|
Parameter |
Description |
|
access-control.name |
The plugin name (plainid). Do not edit this parameter. |
|
plainid.url |
URL to the Runtime service (PDP) https:// (Use http/s to match the Runtime running configuration) |
|
plainid.clientid |
ClientID defined to the Scope used by the querying Application. |
|
plainid.secret |
ClientSecret of the Scope used by the querying Application. |
|
plainid.template |
Name of the relevant Identity Template used for data filtering. |
|
plainid.userField |
The name of the user field that will be sent in the connection. PlainID plugin will use this field name to find the key value pair in the driver extraCredential and will take the value of this pair as the Identity for the Policy Decision request. |
|
plainid.entityAttrPrefix |
All keys in the extraCredentials property starting with this prefix will be parsed and used in the runtime access request with the attribute name as the Key (excluding the prefix) and the value. |
|
plainid.envVarPrefix |
All keys in the extraCredentials which will start with this prefix will be parsed and used in the runtime access request with attribute name as the key without the prefix and the value |
|
plainid.resolution-response-empty |
Defines the default behavior of the table level access.
|
|
plainid.resolution-access-empty |
Defines the default behavior if column-level access is not defined in the Platform.
|
|
plainid.maskFunc |
The masking value that will be used to mask unauthorized columns with data type string. |
|
plainid.cache |
The PlainID Trino Plugin can cache the results of the Policy Decision for quicker responses. The plainid.cache parameter defines the cache TTL ( in seconds). |
Configuration Examples
plainid.clientid=PBU4VTXXXP4TZVLIKPAM
plainid.secret=yNe6SLuuMhUDY1rQTz2bUYdD9GerZzcHNDsvEhbg
plainid.template=CustomerIdentites
plainid.userField=customer-userid
plainid.entityAttrPrefix=entity_attribute
plainid.envVarPrefix=env_var
extraCredential Property
Customer-userid:user123;
entity_attribute.orgID:org9;
env_var.code:T221
Runtime Request from the PlainID Authorizer
{
clientId: PBU4VTXXXP4TZVLIKPAM,
clientSecret: yNe6SLuuMhUDY1rQTz2bUYdD9GerZzcHNDsvEhbg,
entityTypeId: CustomerIdentites,
entityId: user123,
entityAttributes: {
orgID: [ org9
]
},
environment: {
code: [
T221
]
}
You should define the Policies for data filtering both for row level and column level.