Following is an example of the Policy Resolution JSON response for the “accounts” table. The full table being queried, as accessed by an admin (no restriction on the table) appears:
The resulting access for an employee located in the US, for the “account” table outlined above, will look as follows when the full table is queried, and the policy outlined above is in place:
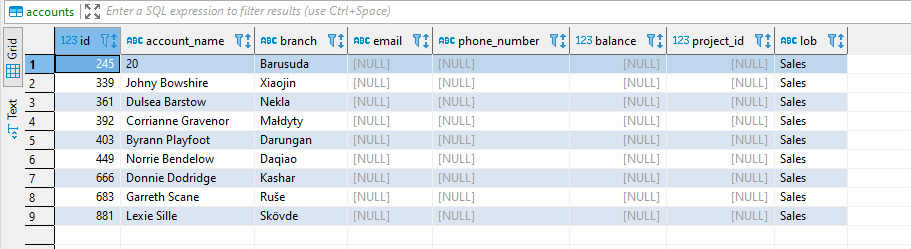
The restricted columns are displayed as NULL, and only the records with the value LOB=”Sales” are displayed.
Add the policyDataMapping Section to the config.json. For each table on which we want to enforce Access Policies, we need to add the table information to the mapping configuration in the PDP config.json:
Sample Response
{
tokenValidity: 0,
response: [
{
access: [
{
path: 14,
attributes: {
tablename: [
accounts
],
level_access: [
2
],
classification: [
public
],
columnname: [
lob
],
uid: [
14
],
databasename: [
testing
]
},
resourceType: Columns_Denodo,
actions: [
{
action: View
}
]
},
{
path: 7,
attributes: {
tablename : [
accounts
],
level_access: [
1
],
classification: [
public
],
columnname : [
id
],
uid: [
7
],
databasename : [
testing
]
},
resourceType: Columns_Denodo,
actions: [
{
action: View
}
]
},
{
path: 8,
attributes: {
tablename : [
accounts
],
level_access: [
2
],
classification: [
public
],
columnname : [
account_name
],
uid: [
8
],
databasename: [
testing
]
},
resourceType: Columns_Denodo,
actions: [
{
action: View
}
]
},
{
path: 9,
attributes: {
tablename : [
accounts
],
level_access: [
1
],
classification: [
public
],
columnname : [
branch
],
uid: [
9
],
databasename: [
testing
]
},
resourceType: Columns_Denodo,
actions: [
{
action: View
}
]
}
],
privileges: {
allowed: [
{
resourceType: testing.accounts,
actions: [
{
action: View,
asset-attributes-filter: {
OR: [
{
OR: [
{
AND: [
{
attribute: lob,
type: STRING,
operator: EQUALS,
values: [
Sales
],
match: any
}
]
}
]
}
]
}
}
]
}
],
denied: []
}
}
]
}
The full table being queried, as accessed by an admin (no restriction on the table):

The resulting access for an employee located in the US, for the “account” table outlined above, will look as follows when the full table is queried, and the policy outlined above is in place:

The restricted columns are displayed as NULL, and only the records with the value LOB=”Sales” are displayed.
Add the policyDataMapping Section to the config.json. For each table on which we want to enforce Access Policies, we need to add the table information to the mapping configuration in the PDP config.json:
JSON Structure
{
"policyDataMapping":[
{
"resourceTypeId":"d98231b9-43e3-4f8d-bea0-e375f0bf803d",
"mapping":[
{
"resourceFullPath":"admin.accounts_private",
"attributes":[
{
"attributeName":"account_owner",
"resourceAttributeName":"account_owner"
},
{
"attributeName":"account_type",
"resourceAttributeName":"acct_type"
},
{
"attributeName":"balance",
"resourceAttributeName":"acct_balance"
}
]
}
]
}
]
}
| Attribute | Description | Notes |
|---|---|---|
| resourceTypeId | The Asset Template GID (see details below for obtaining the GID) | Required |
| resourceFullPath | The full path to the table {database}.{table_name}. this is dependent of the vendor type. The full path may differ between different vendors/authorizers (e.g. Google BigQuery, Denodo, Trino, etc.). |
Required |
| attributeName | The name of the Attribute in the Platform. | Optional |
| resourceAttributeName | The name of the actual column in the table. | Optional |
NOTE: The attributeName and resourceAttributeName are optional in case where there is a full match between the Asset Template Attributes and the physical table column names. So, when specifying just the resourceFullPath the Attributes that are defined in the Asset Template will be used for filtering.
Sample Request
{
"entityId": "xB724129",
"clientId": "P5SUL3MHBHBHB5C0VFD9J",
"clientSecret": "cOtZbPLaHUUHKHKJHKJHgeV02avpkYWvonlG4j",
"environment": {
"database": [
"admin"
],
"table": [
"accounts_private"
],
"resourceFullPath": [
"admin.accounts_private"
]
}
}
Sample Response
{
"tokenValidity": 0,
"response": [
{
"access": [],
"privileges": {
"allowed": [
{
"resourceType": "admin.accounts_private",
"actions": [
{
"action": "View",
"asset-attributes-filter": {
"OR": [
{
"OR": [
{
"AND": [
{
"attribute": "account_type",
"type": "STRING",
"operator": "EQUALS",
"values": [
"basic"
],
"match": "any"
}
]
}
]
}
]
}
}
]
}
],
"denied": []
}
}
]
}