The PlainID Envoy Authorizer is a ready-to-use integration for specific service-mesh technologies, delivered as a sidecar, to control authorization on the service-to-service traffic. The Authorizer supports Envoy Proxy external authentication using its External Authorization (ext_authz) filter.
This allows Envoy to delegate authentication and authorization decisions to the Authorizer.
The Authorizer supports Istio Service Mesh as their traffic management is controlled by Envoy Proxy.
Use Example
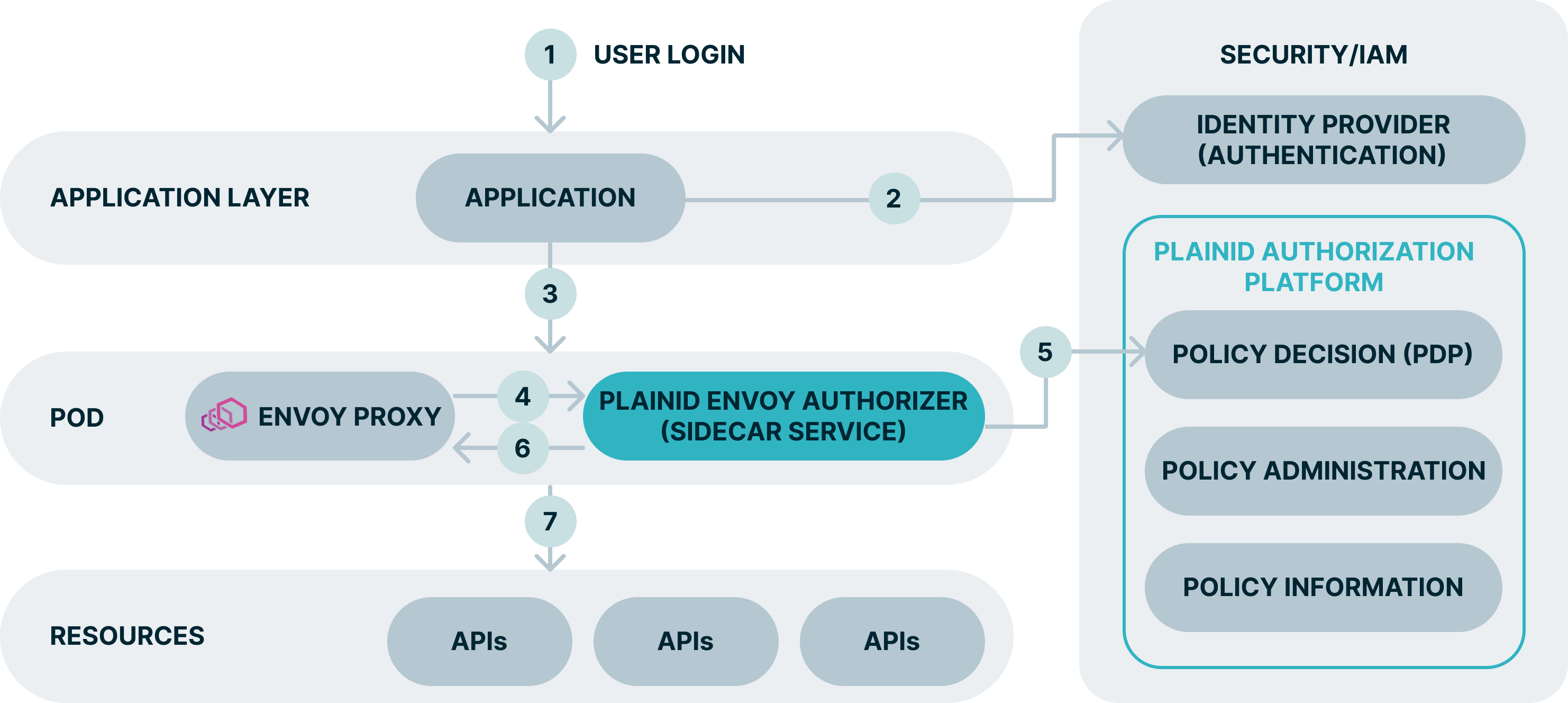
Explanation
- The end user access the app.
- The user is redirected to complete the authentication process on the IDP.
- The API call is intercepted by Envoy API GW.
- The API proxy calls the PlainID sidecar container for an access decision request.
- The PlainID sidecar container requests an access decision from the PlainID PDP, which then responds with a dynamically calculated access decision based on the policies configured within the Platform.
- Access Decisions is enforced at the API GW. Request can be denied, permitted as-is, or permitted with PlainID enriching the access token with further Authorization instructions.
- The client can access API resources and services.
Prerequisites
The following applications are required to install and configure the Authorizer for use with the Platform:
- Kubernetes 1.16+
- Istio 1.15+ (for Istio Service Mesh Integration)
- Helm 3.8.0+
In addition to running the authorizer itself, the Helm Chart is responsible for installing and configuring the Authorizer to integrate with other components. Helm v3.8.0 is required to properly install and configure the authorizer solution with your Kubernetes cluster.
For more information on using Helm Chart, see Helm.
The Policy Authorizer Package Content
| File | Description | Should be updated |
|---|---|---|
| /authz-envoy/templates/crds.yaml | K8s Custom Resource Definitions | No |
| /authz-envoy/templates/manager.yaml | Deployment configuration for authz-operator (plainid-controller-manager) | No |
| /authz-envoy/templates/namespace.yaml | Deployment configuration for authz-operator (plainid-controller-manager) | Optional |
| /authz-envoy/templates/rbac.yam | K8s Namespace configuration for authz-operator (plainid-controller-manager) | Optional |
| /authz-envoy/templates/serviceAccount.yaml | K8s Service Account configuration | Optional |
| /authz-envoy/templates/webhook.yaml | PlainID Mutating Webhook configuration | No |
| /authz-envoy/Chart.yaml | Contains information about the Helm Chart | Yes |
| /authz-envoy/filter.yaml | Envoy configuration example (EnvoyFilter kind) | Yes |
| /authz-envoy/values.yaml | The default configuration values for this chart (AuthZ Operator and Sidecar settings) | Yes |
| /samples/authz_v1_plainidinjector.yaml | AuthZ Sidecar Pod-Injection configuration | No |
| /samples/sidecar-echo.yaml | AuthZ Sidecar configuration example with settings | Yes |
| /images.txt | List of PlainID AuthZ Operator and Sidecar images with tags (versions) | No |