The integration of PlainID with Auth0 allows organizations to implement a seamless Authentication-Authorization process. Auth0, being an IdP (Identity Provider), primarily handles the Authentication process using established protocols like OIDC and SAML, resulting in an authentication token. The PlainID Auth0 Authorizer complements Auth0’s authentication process by calculating and generating a dynamic list of claims and groups based on PlainID’s policies. These claims and groups enrich the token generated by Auth0, providing the user with adaptive access they are entitled to.
The token enrichment flow is aimed at contextually and dynamically calculating and providing a list of Authorizations (claims) to Auth0 during the login process. The outcome is a continuous and adaptive Authorization process that grants users access based on their changing roles and responsibilities within an organization. The PlainID Auth0 Authorizer bridges the gap between Authentication and Authorization, providing a comprehensive solution for organizations to manage user access
The following sections contain detailed instructions for creating, managing, and migrating Auth0 Actions, along with the knowledge and tools necessary to leverage Actions effectively within your Authentication workflows and use them with a PlainID IDP Token Enrichment Authentication flow. Instructions on how to migrate from Auth0 Rules to Auth0 Actions are also detailed below.
Auth0 is phasing out Rules and Hooks. It is strongly recommended that you consult your Auth0 Admin to transition to using Actions, as they will soon replace Rules and Hooks.
Use Example
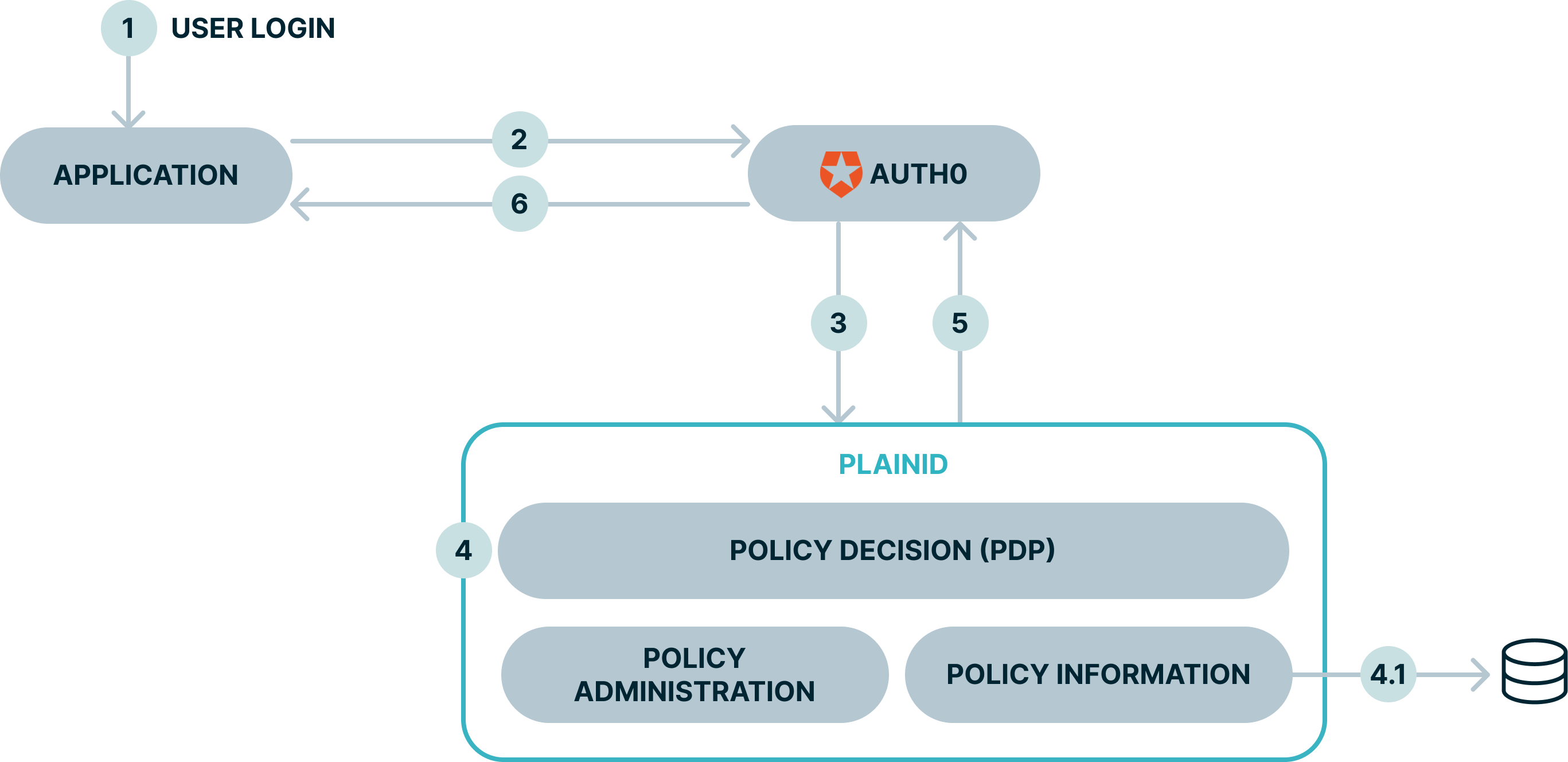
Explanation
- User logins to the application.
- The app initiates an authentication process with Auth0.
- As part of the authentication process, Auth0 sends a request to PlainID via a webhook interface for authorization claims.
- The PDP dynamically calculates the access decision. If needed (4.1), the Policy Information Point (PIP) pulls additional user or asset attributes from various data sources to calculate the access decision.
- PDP returns access decisions containing claims to be used for enriching the access token minted by Auth0.
- Auth0 provides the app with an access token containing the dynamically calculated access decision.
Create an Auth0 Action
An Auth0 Application is required to create an Action. Refer to Auth0's article on how to Write your First Action before continuing.
For more information, see Auth0 Authorizer Configuration.