The PlainID Azure API Management Authorizer enables fine-grained, policy-based access control for APIs managed by Azure API Management (APIM). It provides consistent and centralized enforcement of business Access Policies by integrating with the PlainID Runtime (PDP), which evaluates access in real time.
The Authorizer acts as a Policy Enforcement Point (PEP), intercepting API calls and enforcing the access decision received from the Policy Decision Point (PDP).
Contact our Support Team for access to the Azure API Management Authorizer
Architecture Overview
Authorization Flow Diagram
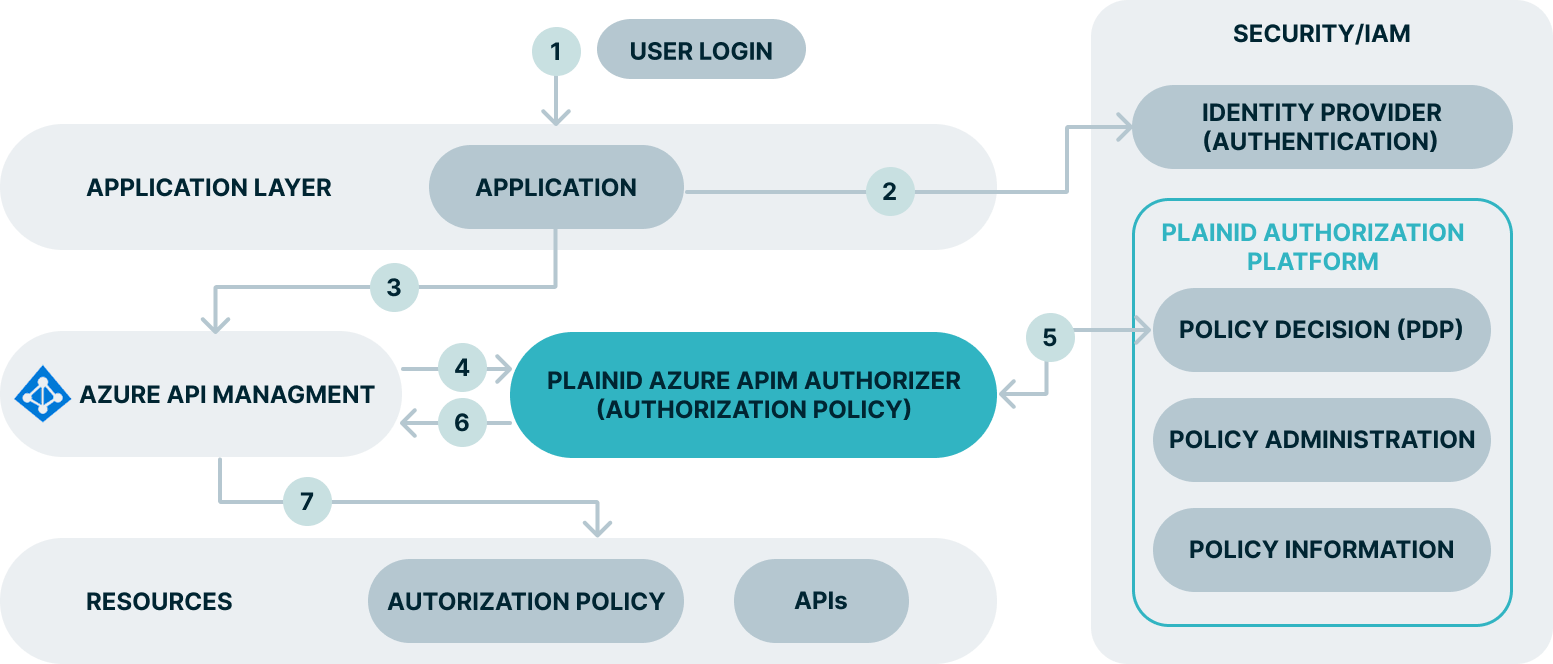
Request Flow
- User logs in and accesses the application.
- The application sends an request to Azure API Management (APIM).
- The PlainID Authorizer (PEP) intercepts the request.
- The Authorizer extracts identity and request context from the call.
- An Authorization request is sent to the PlainID Policy Decision Point (PDP).
- The PDP evaluates Access Policies and returns an Allow or Deny decision.
- The Authorizer enforces the decision, forwarding the request to the backend API or blocking it.
Prerequisites
Before you begin, ensure the following:
- Access to the Microsoft Azure Portal.
- A configured PlainID environment with access to the Runtime (PDP) endpoint.
- A Scope in PlainID with associated client credentials (Client ID and Secret or JWT).
- The necessary API(s) deployed and managed in Azure API Management.
Deployment Instructions
Defining Named Values
In Azure API Management > Named values, create the following keys. Use type = secret for sensitive values such as clientSecret. Refer to Use named values in Azure API Management policies for more information on where to find Named Values and how to use them.
| Name | Description |
|---|---|
clientId |
Client ID from the configured Scope in PlainID. |
clientSecret |
Client Secret from the PlainID Scope (used if authenticationMethod is secret). |
plaindidUrl |
Full URL to the PlainID Runtime endpoint for permit-deny decisions. |
authenticationMethod |
token for JWT-based authentication or secret for client credentials. |
enableTracing |
true to enable trace logs in APIM Analytics. |
onPreventBody |
Body content returned when access is denied. |
onPreventContentType |
Content-Type for denied responses (e.g., application/json). |
onPreventStatusCode |
HTTP status code for denied requests (e.g., 403). |
runtimeFineTune |
JSON structure for tuning the Runtime access request. |
runtimeRequestTimeout |
Timeout value in seconds for the Runtime request (e.g., 60). |
Example Configuration
clientId: PYX9B9H5S29IBG9OEISG
clientSecret: ****
plaindidUrl: https://<host>/api/runtime/5.0/decisions/permit-deny
authenticationMethod: token
enableTracing: true
onPreventBody: { "code": 403, "error": "Forbidden" }
onPreventContentType: application/json
onPreventStatusCode: 403
runtimeFineTune: {
"includeAccessPolicy": "true",
"includeAccessPolicyId": "true",
"includeDetails": true,
"includeAssetAttributes": true,
"includeIdentity": true,
"includeIdentityAttributes": true,
"entityId": "userId",
"entityAttributes": {
"identityattr1": ["identityAtt1Value"]
},
"entityTypeId": "User"
}
runtimeRequestTimeout: 60
Adding the Authorization Policy
- Navigate to the API you want to protect in the Azure Portal.
- Select the Inbound Processing section.
- Click Add policy and choose Other policies.
- Paste the PlainID policy XML into the editor.
- Save your changes.
You can refer to Azure’s official guide for detailed steps.
Alternatively, you can apply the policy at the Product level under:
APIs > Products > [Your Product] > Policies > Inbound Processing