PAA and PIP Settings
PAA and PIP settings are categorized into both global (Tenant) and Environment levels.
Environmental PAA and PIP settings are accessible to designated administrators and viewers, whereas Global PAA and PIP settings are accessible and administrable exclusively by tenant administrators.
PAA
For a variety of reasons, an organization may prefer to have their Policy Decision Point (PDP) as close as possible to their business applications. These reasons may include any or all of the following:
- Increase performance
- Decrease latency (downtime, delays, etc.)
- Increase security
- Prevent sending sensitive organizational data over the Internet
To achieve these goals, you can host components of the Authorization Platform within your network (LAN or Cloud provider such as AWS, Azure, Google Cloud etc.) by configuring one or more PAAs (Policy Authorization Agents) wherever you wish to host it.
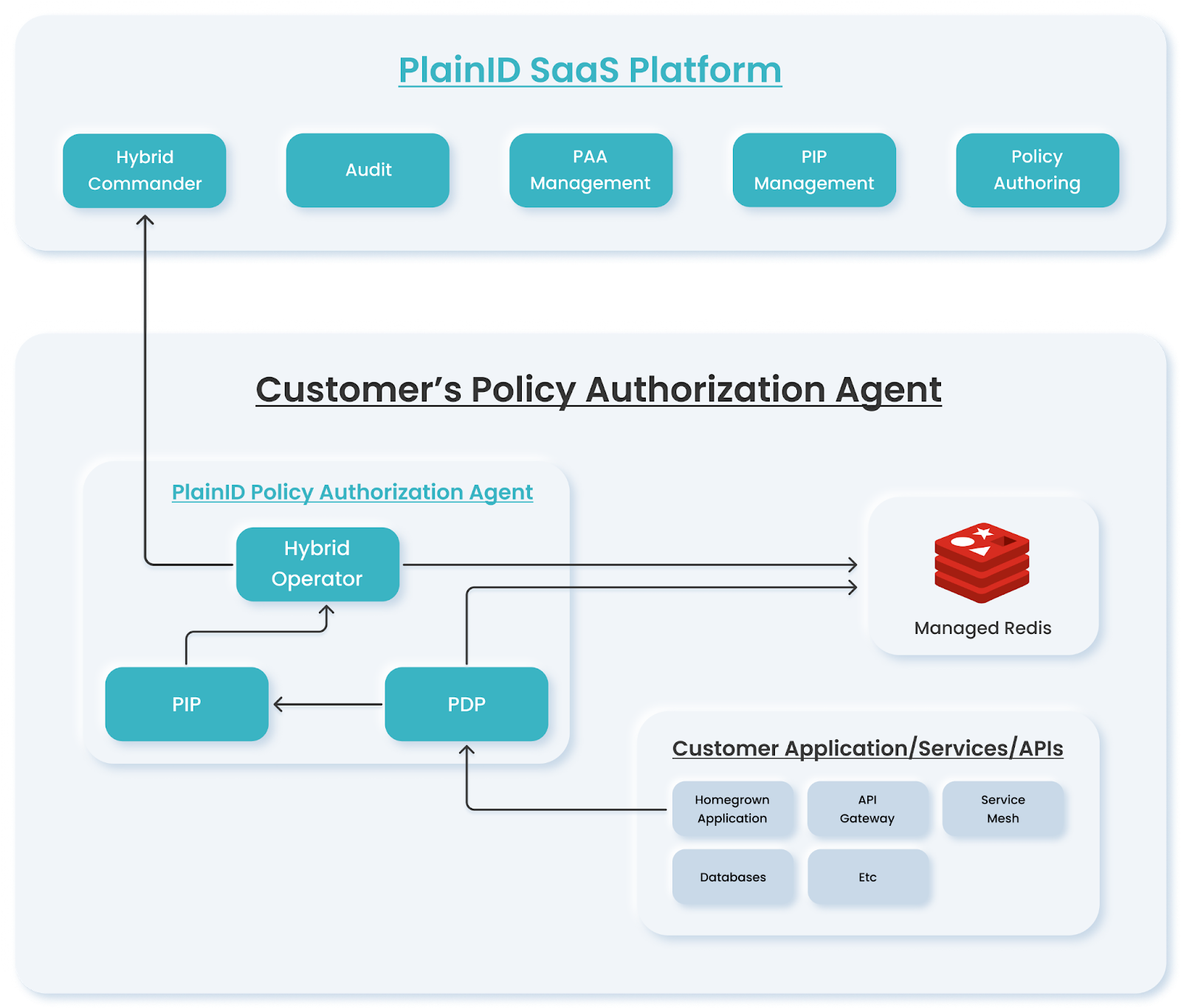
A Policy Authorization Agent is a set of microservices or components that are deployed in your environment. It can be hosted on a local network (delivering increased performance and security, decreased latency and timeouts, etc.) or it can be in a datacenter physically located in close proximity to your organization (also decreasing latency, etc.).
Once you create a PAA, the PAA is listed on the Policy Authorization Agents screen. Each PAA is represented by a Policy Authorization Agent Card.
The PAA consists of the following components:
- Hybrid Agent, responsible for communicating with the Authorization Platform and the Customer-hosted hybrid components.
- PIP (Policy Information Point), responsible for connecting with the various data sources (databases, REST APIs, user repositories, etc.)
- PDP (Policy Decision Point), responsible for providing the runtime authorization decisions, connecting to the Organization's Applications, services and APIs.
- Built-in REDIS, used for local caching and database (in Production environments, it is recommended that you use a managed REDIS)
Sample PAA Workflow
When an organization is maintaining multiple Environments (for example, Staging and Production), it is recommended that a PAA be configured for each Environment, each with its own connection strings.
In this scenario, the decision-making workflow can involve (for example):
- An Application requesting an authorization decision from the local PDP.
- If Identity information is required, the PDP contacts the local PIP to retrieve Identity data from the local data sources.
- The PIP data is returned to the PDP, which sends the decision back to the Application.
- All communication is managed locally, increasing performance and security, protecting sensitive information, and decreasing latency.
Supported Architectures
The PAA can work in a customer-hosted environment through the use of the following tools:
- Kubernetes-based deployment (standard Helm Chart)
- Standalone (Binary/Service)
End-to-End Workflow
An end-to-end workflow of configuring a Policy Authorization Agent to manage communication and authorization decisions locally would include the following steps:
- Create a PAA
- Download the PAA bundle
- Install and configure the PAA
- Defining a Data Source
- Defining a View for the Data Source
- Assign the PAA to an Environment and/or Scopes
- Create a new Asset Type
- Associate the Asset Type Attributes
For more information, see Managing Policy Authorization Agents.
Viewing Policy Authorization Agent Details
At any time, you can view details of a PAA by clicking on the PAA Card in the Policy Authorization Agents screen (Tenant Settings > Policy Authorization Agents).
The Policy Authorization Agent Details side panel opens, displaying the following information:
- Name of the Policy Agent (which is editable, enabling you to change it, if needed)
- Agent ID number
Click Copy to copy the Agent ID number.
Click Save if you changed the PAA name.
Policy Authorization Agent Cards
Multiple PAAs can be created within a Tenant. Each PAA is listed in the Policy Authorization Agent list, located on the Policy Authorization Agent tab of the Tenant Settings screen.
The first PAA card that appears on the Policy Authorization Agent tab is the built-in PAA that contains a PDP component (Cloud-based Authorization Platform with all components hosted in the Cloud). Additional PAAs appear in alphabetical order, each containing the following information:
- PAA Name
- PIP icon, which is visible when the PAA is connected to one or more PIPs. If no PIPs have been connected to this PAA, the PIP icon is not displayed.
- PDP icon indicates that a PDP has been connected to the PAA.
- Download button enables you to download an installation bundle for the PAA. Bundle options include: Helm and Standalone.
PAA and PIP Administration Audit
Users can access PAA and PIP Admin Audit Events through the Administration Audit Reports article.