Initial Setup Example
Please note - the follwing steps, examples, and screenshots might differ according to Azure Administration Console version, and are here to illustrate the overall setup process.
Prerequisites - External IDP setup
During the initial tenant setup the AAD was already set up as the tenant IDP according to the instructions on this page, Configuring an IDP for the Tenant.
As part of this initial setup you also already created an enterprise application in Azure AD. Contact your IDP admin for support if needed. For reference this is the Enterprise Applications page in AAD:
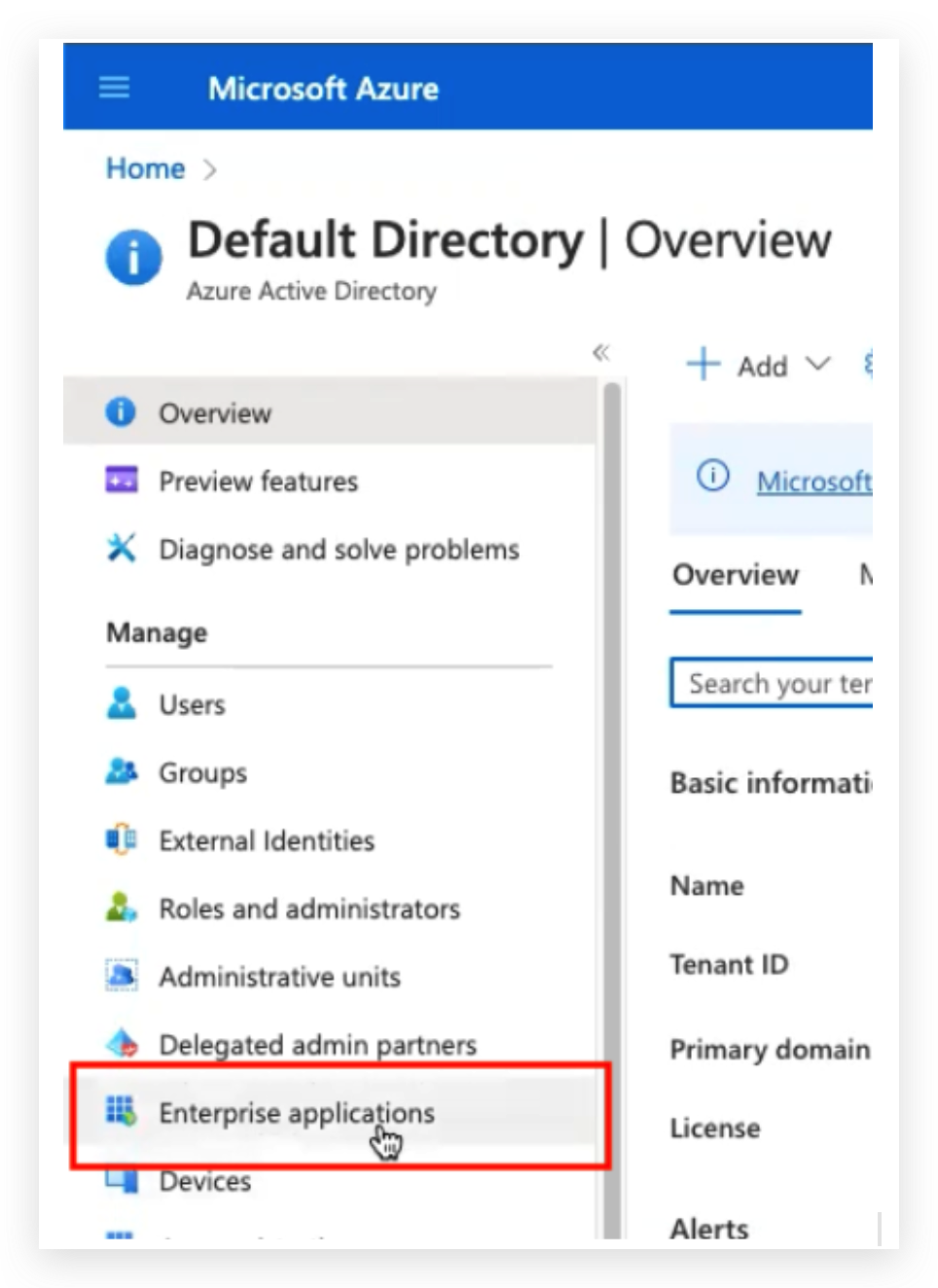
You will be navigated to the Enterprise Applications page:
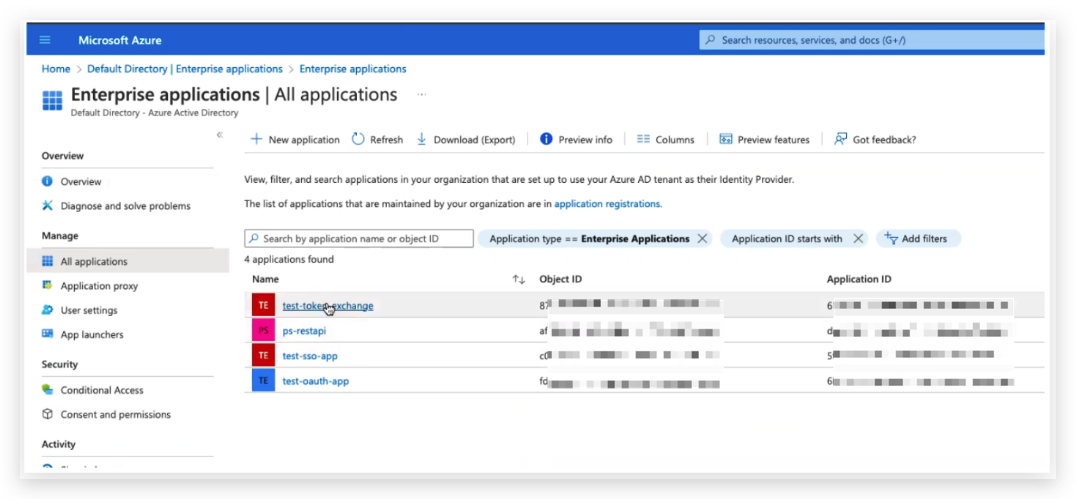
Set up the Application SSO Claim
- Open you AAD management UI.
- Goto Enterprise Application, find your application in the list and choose your application.
- In the application page choose the Single sign-on menu:
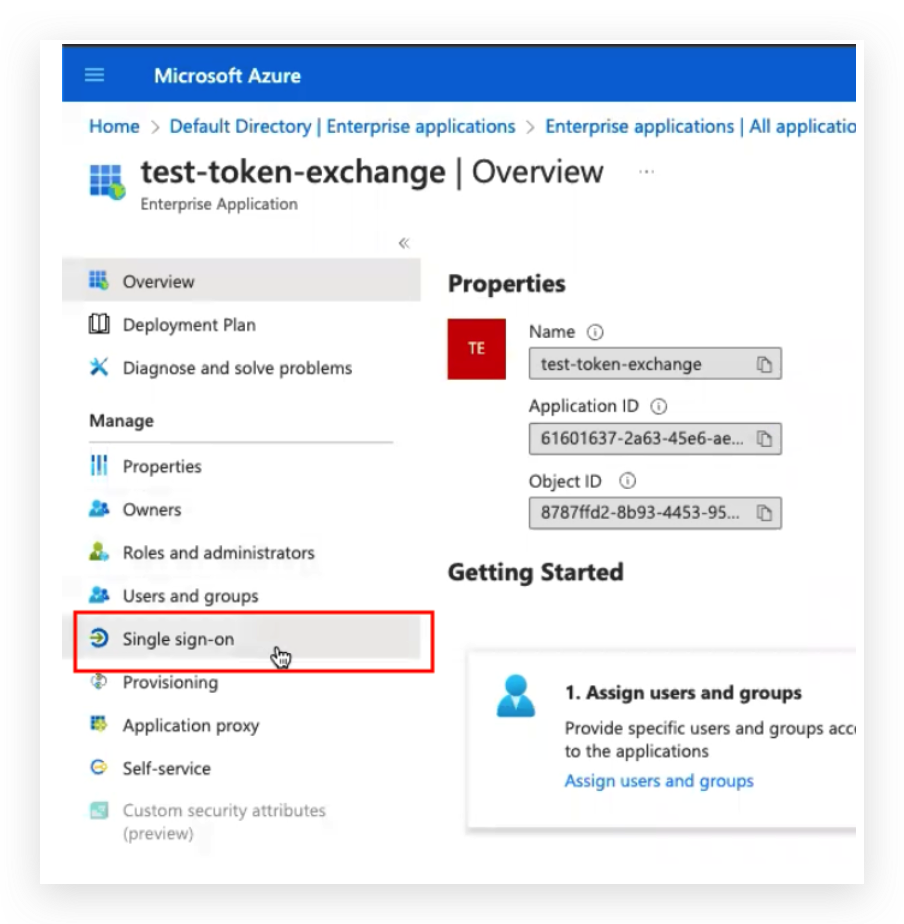
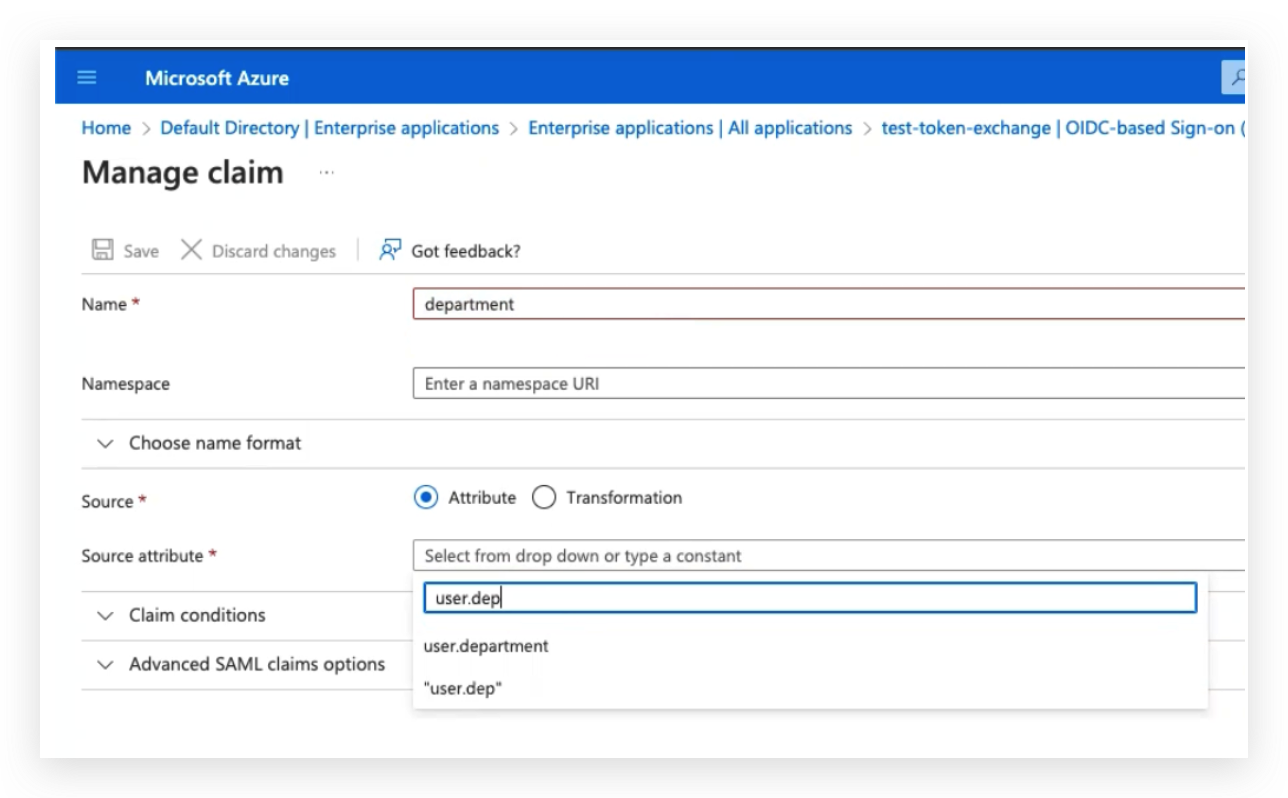
- Enter the manage Attributes & Claims
- Add a new claim with the claim name that was set in PlainID tenant settings
- Choose the source attribute for the value of the new claim and save your changes
Azure Active Directory IDP token endpoint example
You can now call Azure Active Directory token endpoint with user credentials and get an id_token (Check the Response example below). With this id_token you will call PlainID for token exchange and then use the new token to call the Admin APIs.
Use the following Azure endpoint to get a token https://login.microsoftonline.com/<AZURE_AD_TENANT_ID>/oauth2/v2.0/token
Request example with password grant_type
curl --location --request POST 'https://login.microsoftonline.com/<AZURE_AD_TENANT_ID>/oauth2/v2.0/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Cookie: fpc=AuOThG_szTpCkB9hOJwN24UETJLuAQAAACOtktsOAAAA; stsservicecookie=estsfd; x-ms-gateway-slice=estsfd' \
--data-urlencode 'client_id=AAD_APP_CLIENT_ID' \
--data-urlencode 'scope=user.read openid profile offline_access' \
--data-urlencode 'client_secret=AAD_APP_CLIENT_SECRET' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'username=AAD_USER_TO_AUTHENTICATE' \
--data-urlencode 'password=AAD_USER_PASSWORD'
Response example
{
"token_type": "Bearer",
"scope": "email openid profile User.Read",
"expires_in": 4730,
"ext_expires_in": 4730,
"access_token": "ey...",
"refresh_token": "...",
"id_token": "ey..."
}