Policy Points and the Policy Agent are key components that work together to enforce access control policies, ensuring secure processes within an organization's environment. They offer enhanced security through granular access control policies which reduces the risk of unauthorized access. Their architecture simplifies administration processes for policy creation, enforcement, and monitoring. Through these points, organizations can adapt access control policies without disrupting operations and compromising security. You can see the explanation for each service under the diagram:
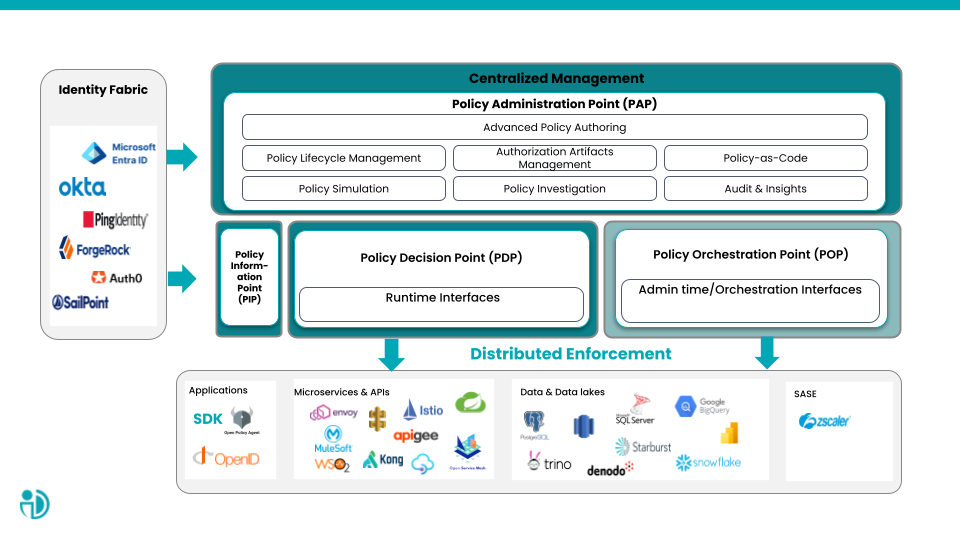
Policy Administration Point
The Policy Administration Point (PAP) is responsible for managing the life-cycle of policies, which includes policy authoring, managing, testing, analyzing, and version control.
Policy Decision Point
The Policy Decision Point (PDP) is responsible for calculating the required Access Decision based on a collection of attributes sent through an authorization request, which are pulled from external repositories and environmental attributes. The Access Decision is calculated based on the policies associated with the request.
The PDP is designed to support different access patterns, which provides defined policies with more consistency and applications with more flexibility.
Policy Orchestration Point
Policy Orchestration Points (POPs) define the connection between the Authorization Platform Tenant and the Vendor Tenant, typically running a third-party application.
Policy Enforcement Point
The Policy Enforcement Point (PEP) enforces policy decisions made by the PDP. It is a response to an access request and can be implemented within the application or as an external component that serves as an authorizer in an application or data extraction.
Policy Information Point
The Policy Information Point (PIP) is a standalone service in the Platform. It is a source of attributes that the PDP uses to address authorization requests based on defined policies. The PIP in PlainID is mapped by a virtualization layer that enables the usage of multiple sources (including virtual and API-based sources) simultaneously.
You can use the PIP service when you need data to support a Policy decision through data from external sources.
For more information on PIPs and how to manage them, click here.
Policy Authorization Agent
The Policy Authorization Agent (PAA) is a set of microservices or components that are deployed within an environment that promotes the integration of external data sources and increases security, performance, stability, and flexibility in Policy enforcement.
The PAA consists of the following components:
-
A Hybrid Agent responsible for communicating with the Platform and the Hybrid Agent Key components.
-
A PIP responsible for connecting with the various data sources (databases, REST APIs, user repositories, etc.).
-
A PDP responsible for providing the runtime authorization decisions and connecting to the organization's Applications, services, and APIs.
-
A Built-in REDIS used for local caching and database (using a managed REDIS is recommended in Production environments).
The PDP (located inside the PAA) can be hosted on a local network or in a physical data center in close proximity to an organization or business. Organizations may prefer to have their PDP as close to their business as possible because it can:
-
Increase security
-
Prevent sensitive organizational data from being sent over the internet
-
Increase performance
- The PAA is delivered and runs in containers which simplifies staged rollouts, auto-scaling, and other operational benefits of a containerized system.
-
Decrease latency (downtime, delays, etc.)
- All communication with the PAA control plane is asynchronous and does not happen as part of processing client API requests.
-
Efficiently process APIs
- Although it is possible to process internal APIs using the PlainID Cloud PDP, you can achieve reduced latency and efficiency with a hybrid PAA, which makes processing internal APIs with a hybrid PAA an attractive option. Part of this efficiency is achieved because your API gateway runs on-premises, near your backend services. In addition, you can increase your adoption of the API Gateways Authorizers by processing internal APIs through the local PDP.
-
Allow for greater control
- Many enterprises are embarking on a hybrid strategy. The ability to manage API runtimes deployed in private data centers is a key requirement for large enterprises. The PAA can be deployed to a cloud or in private data center.
To learn more about installing and deploying PAAs, click here.