Access Control Policies are typically attached to an Application and together define the business logic of who can access and use the Application. Certification is the process of re-evaluating and approving the access controls in place.
Certification processes help identify and mitigate risks associated with unauthorized access to sensitive information. By certifying Policies, organizations can proactively address potential vulnerabilities and strengthen their overall security posture.
Prerequisites
For the Profile Certifying process, it is recommended that you have Environment Admin Client keys specifically for the Environment within which the Applications are being certified.
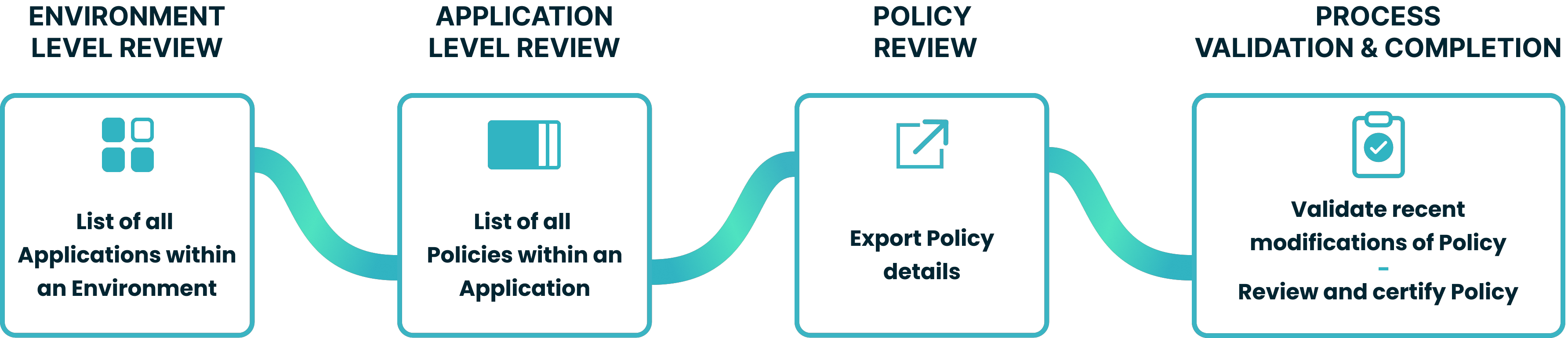
Certification Process Steps
The certification process includes:
- Environment level review
- Application level review
- Policy review
- Process validation and completion
For more information, see: Policy Certification Process.