About the Asset Context Capability
The assetContext capability enhances access control by considering contextual information related to Assets when making Authorization decisions. It allows for a more granular control by incorporating factors like relationships between Assets and contextual parameters. This enables more precise and adaptive access control Policies, improving security and compliance.
Data access through Applications is a common use case in which assetContext can provide significant benefits. Data Access Policies can also incorporate contextual information to determine access more effectively.
Utilizing the assetContext Capability
The assetContext capability is implemented across all Authorization endpoints, which enhances the Policy Decision Point (PDP) by incorporating assetContext in the decision-making process. Through this capability, the PDP conducts further filters the response, taking into account the assetContext, and retrieves the response accordingly.
The assetContext capability provides several additional benefits in terms of access decision-making:
-
Optimized Filtering: By incorporating assetContext, the access decision-making process becomes more optimized and targeted to the specific Application's needs. The capability allows for a more refined and adaptable access control, enabling the system to tailor the response based on the Contextual Assets or Attributes associated with the Asset.
-
Flexibility and adaptability: The assetContext capability allows for dynamic adjustment of access based on the context of the requested Asset. This makes the access decision-making process flexible and can be particularly useful in dynamic or evolving Environments. This flexibility enables organizations to adapt their access control mechanisms to changing business requirements and data contexts without significant reconfiguration or changes to the underlying infrastructure.
Asset Context Capability Sample Use Case
AccountMan is a web-based application used by a financial organization to manage customer accounts. The application allows authorized users to view and update account information based on their assigned roles. The extent of access granted is determined by the classification of data, ensuring that users can only access specific accounts and view designated fields based on their authorized permissions.
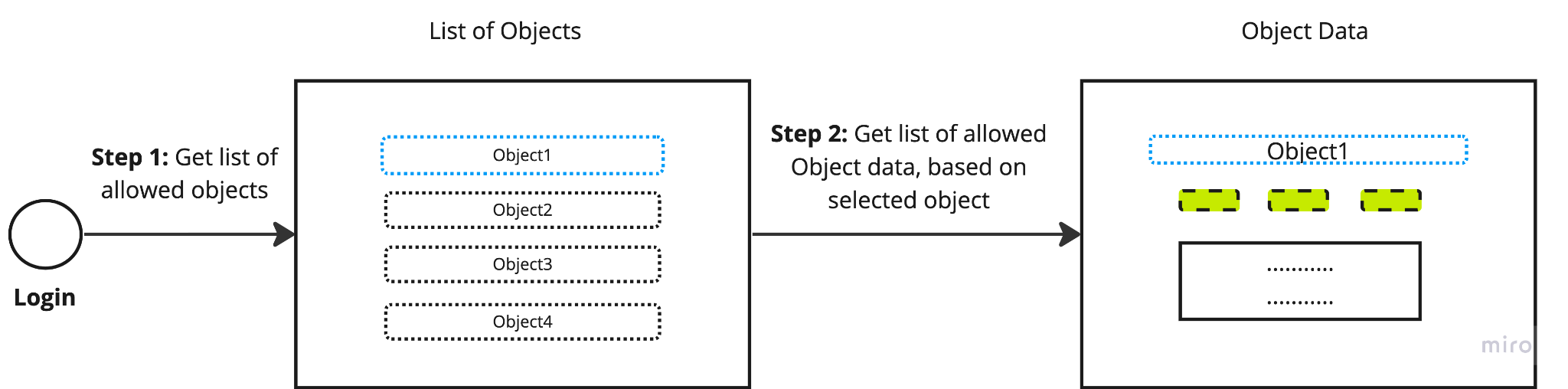
Authorization Flow
The flow below illustrates AccountMan’s Application Authorization flow. In Step 1, users can see a list of permitted accounts (objects). In Step 2, they can navigate to a specific account and depending on their permissions, view specific fields in the account.
Sample Policies
-
HR Employees or Managers can access Public Accounts and non-sensitive Account fields.
-
Managers can access Private Accounts and personally identifiable information fields(PII).
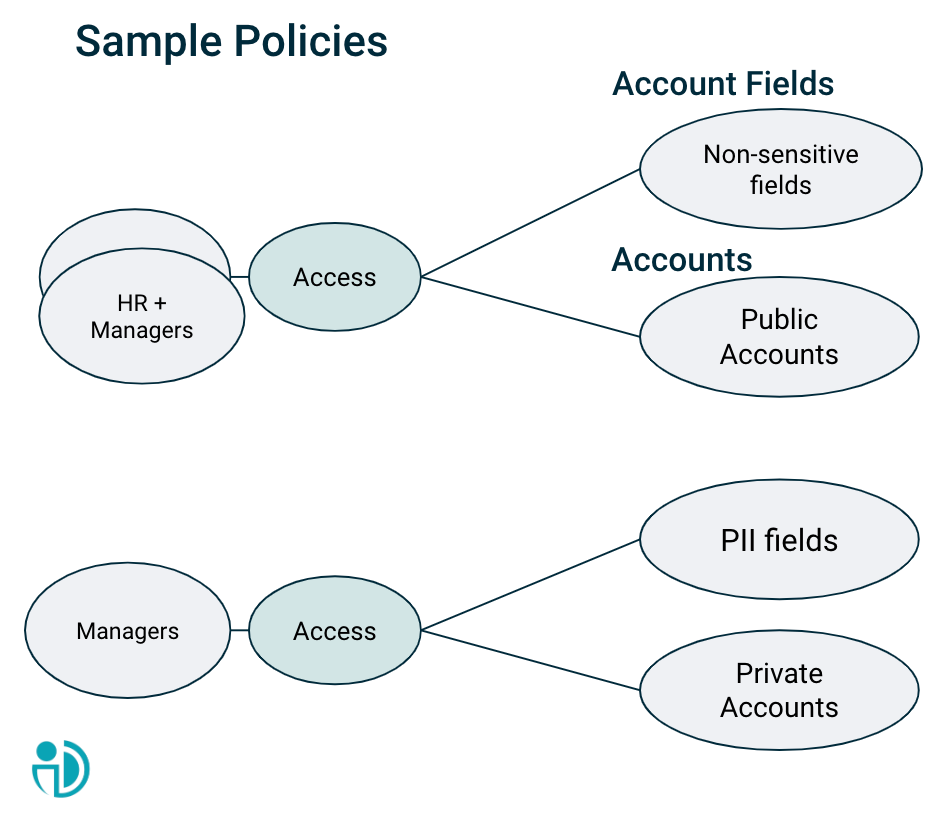
For instance, a manager in the organization may have access to both Public and Private accounts. However, the fields visible to the manager within each classified account may vary. In a public account (e.g., acc1), the manager may be able to see the ID, name, and description fields. In contrast, in a private account (e.g., acc2), the manager may have access to fields such as balance, currency, and owner, which could be classified as PII fields.
Sample Data
Accounts
| ID | Security_classification |
|---|---|
| acc1 | Public |
| acc2 | Private |
Account Fields
| Field ID | Field Classification |
|---|---|
| account_name | non-sensitive |
| account_desc | non-sensitive |
| account_id | non-sensitive |
| account_balance | PII |
| account_currency | PII |
| account_owner | PII |
Sample Request and Response
The following example demonstrates how the assetContext capability is used within the User Access Token endpoint. In this scenario, the Authorization query revolves around determining which account fields a user with a manager role can access, specifically within the context of acc1.
The response indicates that the manager has access to non-sensitive classified Account fields because acc1 is classified as public:
{
"entityId": "Manager_user",
"clientId": "******",
"clientSecret": "********",
"assetContext": [
{
"resourceType": "Accounts",
"path": "acc1",
"action": "ACCESS"
}
]
}
{
"data": [
{
"assetContext": {
"resourceType": "Accounts",
"path": "acc1"
},
"output": {
"accessResponse": {
"tokenValidity": 0,
"response": [
{
"access": [
{
"path": "account_name",
"attributes": {
"path": [
"account_name"
],
"fieldClassification": [
"non-sensitive"
]
},
"resourceType": "account_fields",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_desc",
"attributes": {
"path": [
"account_desc"
],
"fieldClassification": [
"non-sensitive"
]
},
"resourceType": "account_fields",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_id",
"attributes": {
"path": [
"account_id"
],
"fieldClassification": [
"non-sensitive"
]
},
"resourceType": "account_fields",
"actions": [
{
"action": "ACCESS"
}
]
}
]
}
]
},
"error": ""
}
}
],
"contextData": null
}
The assetContext capability allows for the inclusion of multiple assetContext objects within a single request, generating individual contextual responses for each object provided. PlainID enhances this process with optimizations for handling large assetContext datasets and groups similar results for streamlined responses. See further details on the Optimized assetContext Calculation and an example request and responses below.
Applying combinedMultivalue on the assetContext Capability
When used with assetContext requests, the combinedMultiValues capability in the PDP enables handling complex Authorization scenarios where preserving Identity data relationships is essential.
When both capabilities are applied, Identity data relationships remain intact throughout Asset Context calculations. This ensures consistency across Identity evaluation, Asset evaluation, and overall Authorization decisions.
If an Identity has multiple attributes with multiple values, combinedMultiValues maintains the relationship between those values. As a result, Identity permutations are evaluated separately during Policy enforcement, directly impacting Asset Context evaluation:
- If no Identity permutation qualifies for a given Asset Context object, the PDP denies access.
- If only specific Identity permutations qualify, only those are considered when evaluating Asset types associated with Policies.
For more details, see Working with CombinedMultiValues.
Optimized assetContext Calculation
The assetContext calculation is optimized to handle large sets of assets sent in the request as assetContext. This optimization processes them in bulk instead of one at a time, managing similarities and sets of responses. It is mainly significant when processing large data sets and results in faster calculation and response times.
Additional optimization is available in the response processing, handling large responses by optimizing the payload size and thus decreasing response generation time after the calculation and reducing network overheads. This additional response optimization requires users to opt in with a new request flag as it changes the response structure.
To allow users to opt in, a new parameter, useOptimizedAssetContextResponse, has been added to control the response structure. This parameter controls the response structure depending on if users have enabled it or not. If set to true, the response uses an optimized structure that reduces the response payload size and network overheads and improves the overall performance. If set to false or omitted completely, the parameter will not be enabled, preserving the same structure for backwards compatibility.
Additionally, the optimized response only uses keys. PlainID recommends using keys when working with assetContext to simplify the structure and ease the integration. If there are keys provided in the request, they will be returned in the response. If keys are not provided, a string concatenation of all context parameters are used as the unique key.
This optimization not only reduces the amount of data exchanged but also enhances the efficiency of both the system and the network. Below is a request and two response examples. Note that the first response example is not optimized, while the second is optimized:
Request Example
{
"entityId": "user1",
"entityTypeId": "newid",
"clientId": "*******",
"clientSecret": "*********",
"useOptimizedAssetContextResponse":true,
"assetContext": [
{
"key": "account1026",
"resourceType": "account1000",
"path": "account1026",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer3"
]
}
},
{
"resourceType": "account1000",
"path": "account1132",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer3"
]
}
},
{
"key": "account1113",
"resourceType": "account1000",
"path": "account1113",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer86"
]
}
},
{
"resourceType": "account1000",
"path": "account1114",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer86"
]
}
}
]
}
Response (not optimized)
{
"data": [
{
"assetContext": {
"resourceType": "account1000",
"path": "account1132",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer3"
]
}
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": [
{
"access": [
{
"path": "account_customerName",
"attributes": {
"path": [
"account_customerName"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_currency",
"attributes": {
"path": [
"account_currency"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_customerId",
"attributes": {
"path": [
"account_customerId"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_balance",
"attributes": {
"path": [
"account_balance"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_owner",
"attributes": {
"path": [
"account_owner"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
}
]
}
]
}
}
},
{
"assetContext": {
"resourceType": "account1000",
"path": "account1114",
"action": "ACCESS",
"assetAttributes": {
"customerId": [
"customer86"
]
}
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": []
}
}
},
{
"assetContext": {
"key": "account1026"
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": [
{
"access": [
{
"path": "account_customerName",
"attributes": {
"path": [
"account_customerName"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_currency",
"attributes": {
"path": [
"account_currency"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_customerId",
"attributes": {
"path": [
"account_customerId"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_balance",
"attributes": {
"path": [
"account_balance"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_owner",
"attributes": {
"path": [
"account_owner"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
}
]
}
]
}
}
},
{
"assetContext": {
"key": "account1113"
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": []
}
}
}
],
"contextData": null
}
Response Example (Optimized)
{
"data": [
{
"assetContext": {
"keys": [
"{\"resourceType\":\"account1000\",\"path\":\"account1114\",\"action\":\"ACCESS\",\"assetAttributes\":{\"customerId\":[\"customer86\"]}}",
"account1113"
]
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": []
}
}
},
{
"assetContext": {
"keys": [
"account1026",
"{\"resourceType\":\"account1000\",\"path\":\"account1132\",\"action\":\"ACCESS\",\"assetAttributes\":{\"customerId\":[\"customer3\"]}}"
]
},
"output": {
"error": "",
"accessResponse": {
"tokenValidity": 0,
"response": [
{
"access": [
{
"path": "account_customerName",
"attributes": {
"path": [
"account_customerName"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_currency",
"attributes": {
"path": [
"account_currency"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_customerId",
"attributes": {
"path": [
"account_customerId"
],
"classification": [
"PII"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_balance",
"attributes": {
"path": [
"account_balance"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
},
{
"path": "account_owner",
"attributes": {
"path": [
"account_owner"
],
"classification": [
"PII data"
]
},
"resourceType": "Company_Account_Attributes",
"actions": [
{
"action": "ACCESS"
}
]
}
]
}
]
}
}
}
],
"contextData": null
}
In summary, the assetContext capability provides benefits such as enhanced granularity, simplified implementation, alignment with business logic, improved performance, and flexibility in access decision-making. These benefits contribute to more robust and efficient access control mechanisms, supporting organizations in effectively managing and securing their data assets.