General
Authentication to use the PlainID Policy Decision Point APIs can be done by passing the ClientID and ClientSecret in the following methods:
- As part of the REST API Request Body.
- As part of the REST API Request Header.
- As part of a valid JWT that can be verified using the JWT Issuer's JWKS URL.
Using the Authorization Request Body
Sample Request Body for the Permit/Deny Endpoint
Request URL
https:///acme-finance.us1.plainid.io/api/runtime/permit-deny/v3
Request Body
{
"entityId": "UX-12345",
"entityTypeId": "bank_users",
"clientId": "{ClientID}",
"clientSecret": "{ClientSecret}",
"responseType": "accessDecision",
"listOfResources": [
{
"resourceType": "Accounts",
"resources": [
{
"action": "Access",
"path": "AS-XX-12575"
}
]
}
]
}
Using the Authorization Request Header
By adding the following headers to the Authorization Request:
| Header Key | Header Value |
|---|---|
| X-Client-Id | The PlainID Scope ClientID |
| X-Client-Secret | The PlainID Scope ClientSecret |
Using the Authorization Request JWT
PlainID Policy Decision Point can also authorize access to the Authorization APIs.
Please note - the clientIdand entityId must be passed as part of the Authorization Request Body or Header.
The JWT should be valid - the Policy Decision Point will validate the JWT by using the JWKS URL of the JWT Issuer (Authorization Server, IDP, etc.).
If the JWT is invalid - no identity attributes are extracted to be used in the Policy Decision calculation.
The JWKS URLs can be configured in the PlainID Policy Administration Point under Tenant Management > Policy Authorization Agents.
Sample JWT
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022,
"businessData": {
"department": "Home Loans",
"branch": "TX"
},
"phoneNumbers": [
{
"type": "land",
"number": "0123-4567-8888"
},
{
"type": "mobile",
"number": "0333-4567-9999"
}
]
}
Encoding and Decoding of JWT can be done by accessing https://jwt.io
Using the JWT as Identity Attribute Source
The Claims from the JWT can be used to obtain information about the Identity (the user).
The unique identity of the user (entityId) is still required in the request body when using JWT as an identity source.
In the PlainID Policy Administration Point access the Identity Workspace, and map the relevant claims from the JWT to the corresponding Identity Attributes:
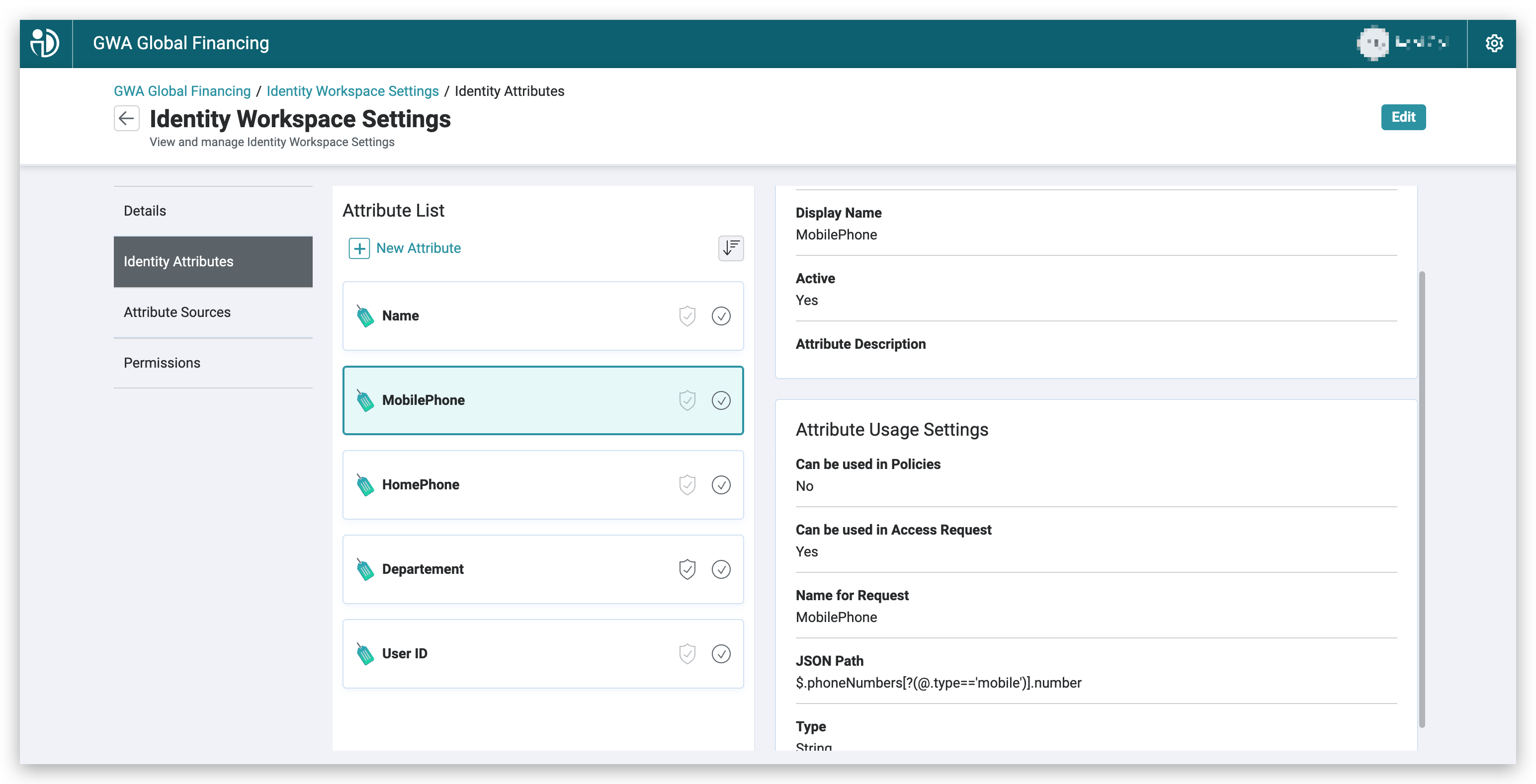
Sample JWT Claims Mapping to Identity Attributes
| Identity Attribute | Claim Name | JSON Path | Value |
|---|---|---|---|
| Name | name | $.name |
John Doe |
| Departement | department | $.businessData.departement |
|
| HomePhone | phoneNumbers | $.phoneNumbers[:1].number The first value from the |
0123-4567-8888 |
| CellPhone | phoneNumbers | $.phoneNumbers[?(@.type=='mobile')].numberThe value with the type |
0333-4567-9999 |